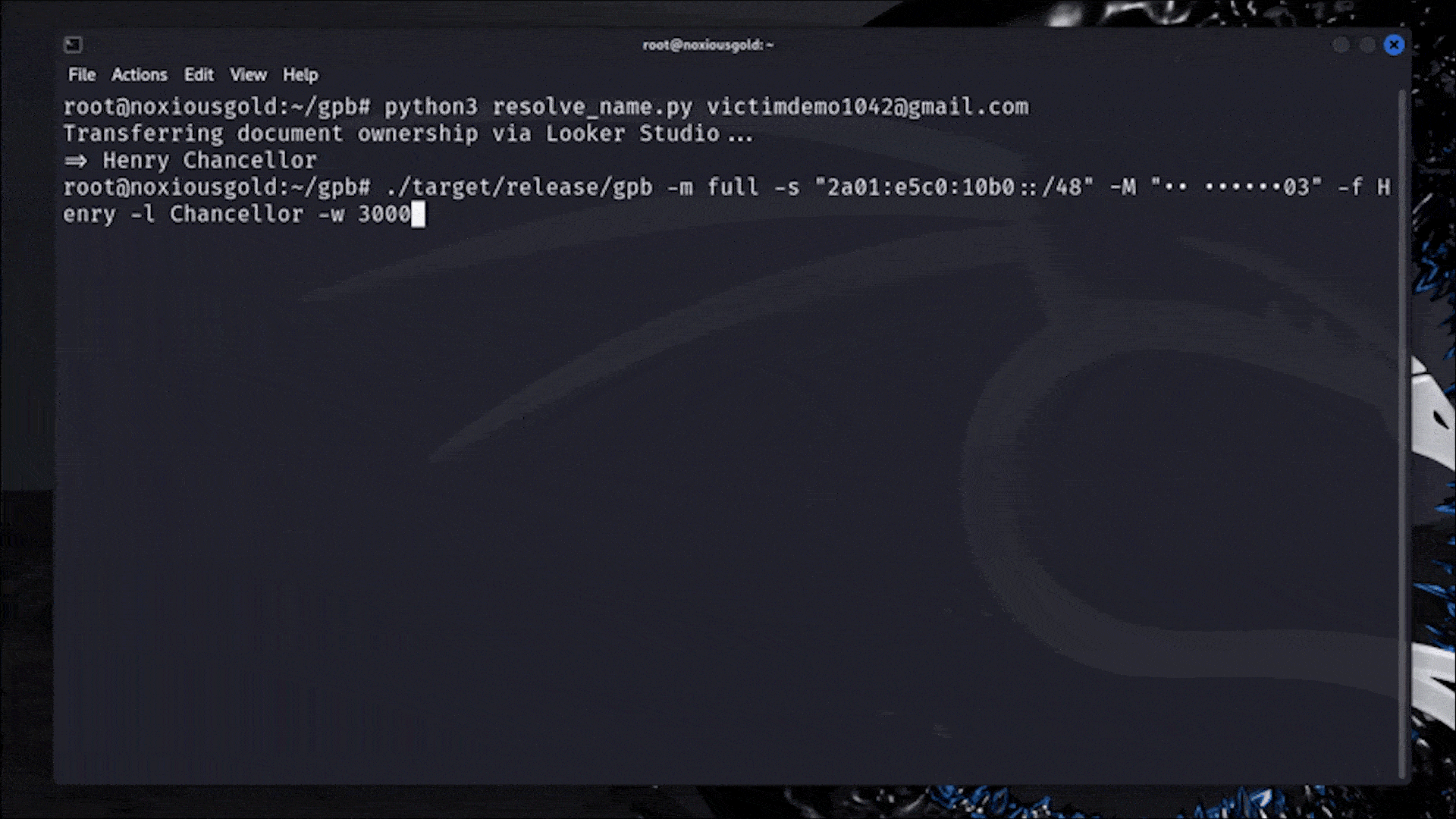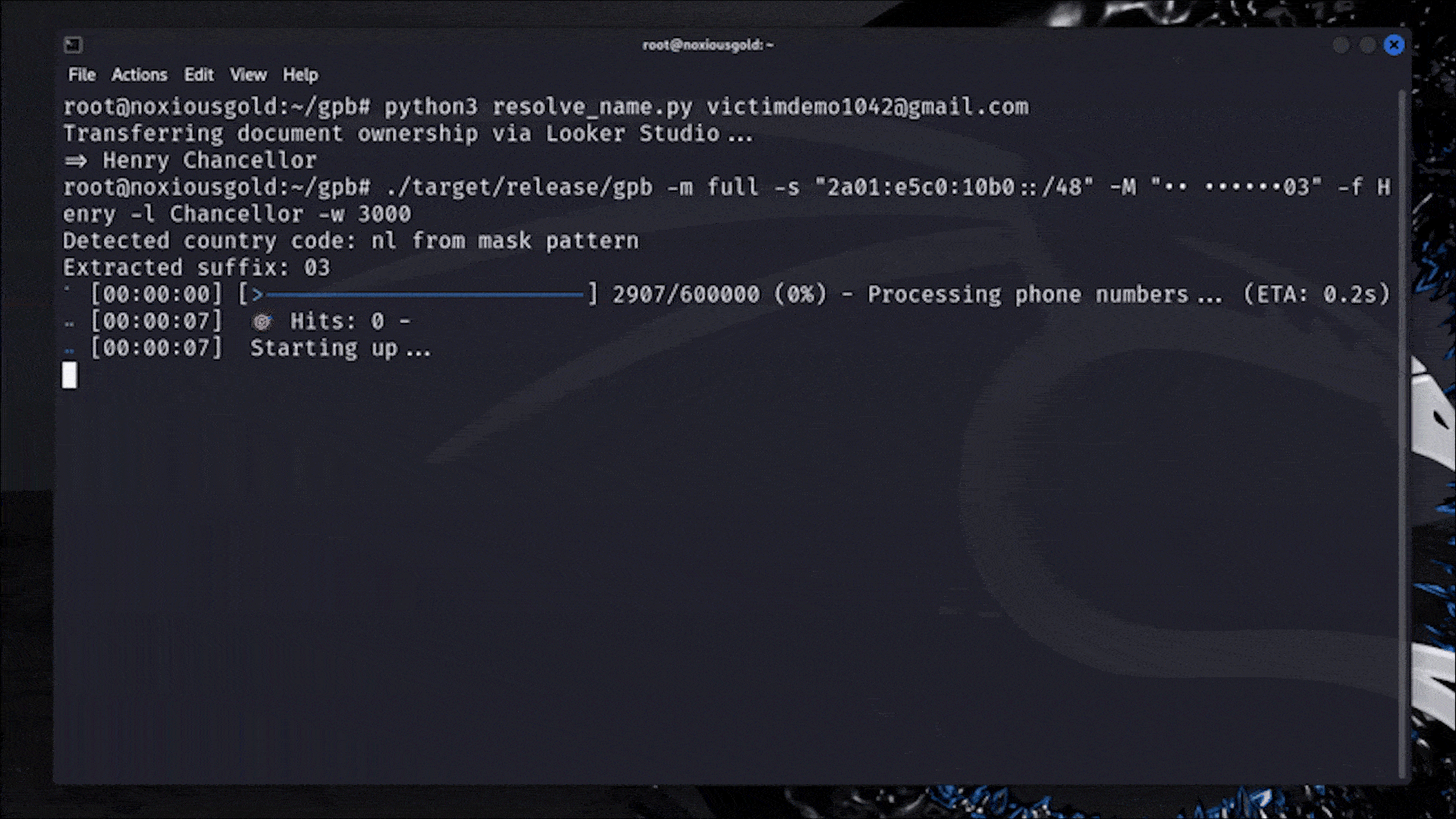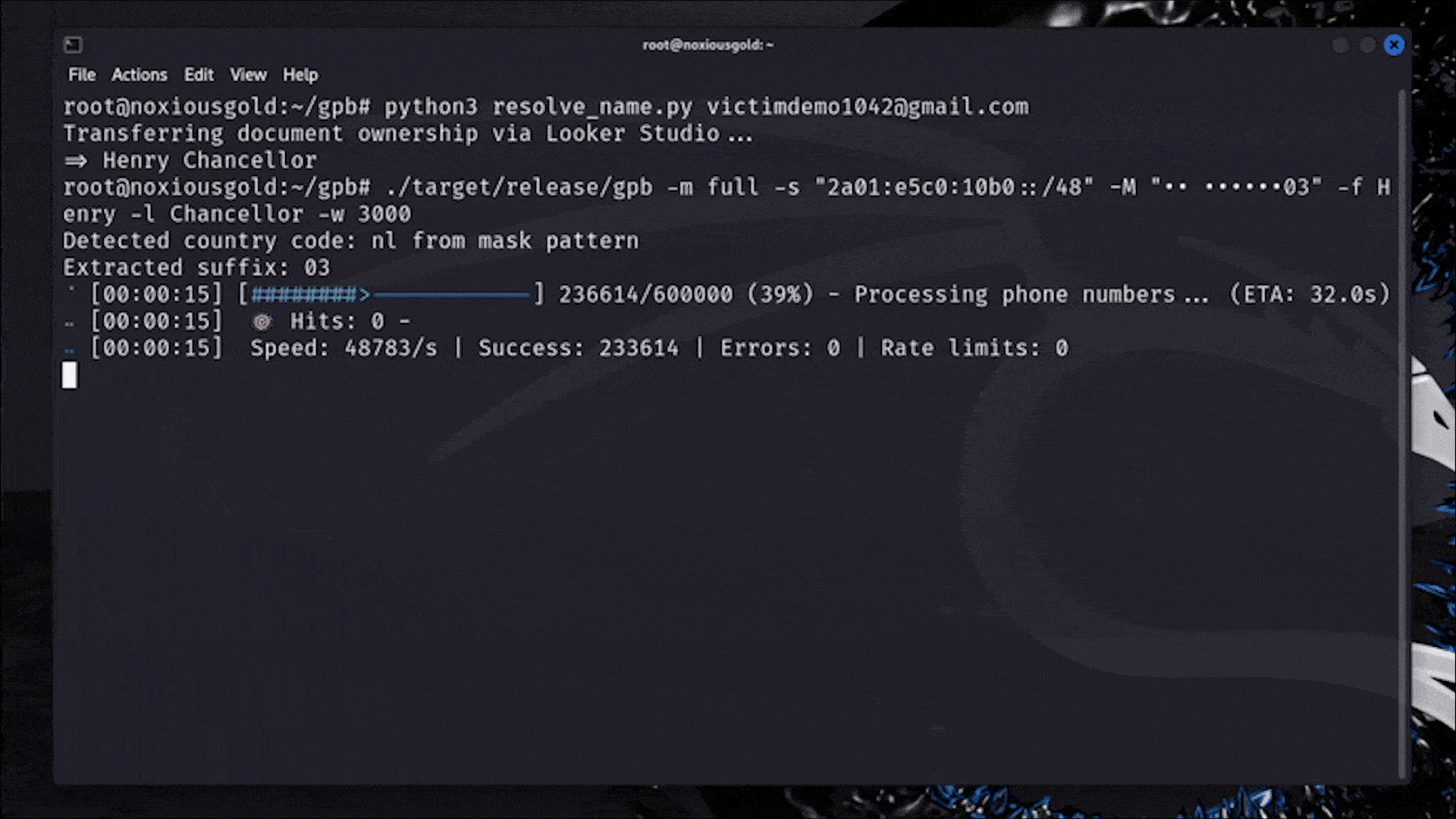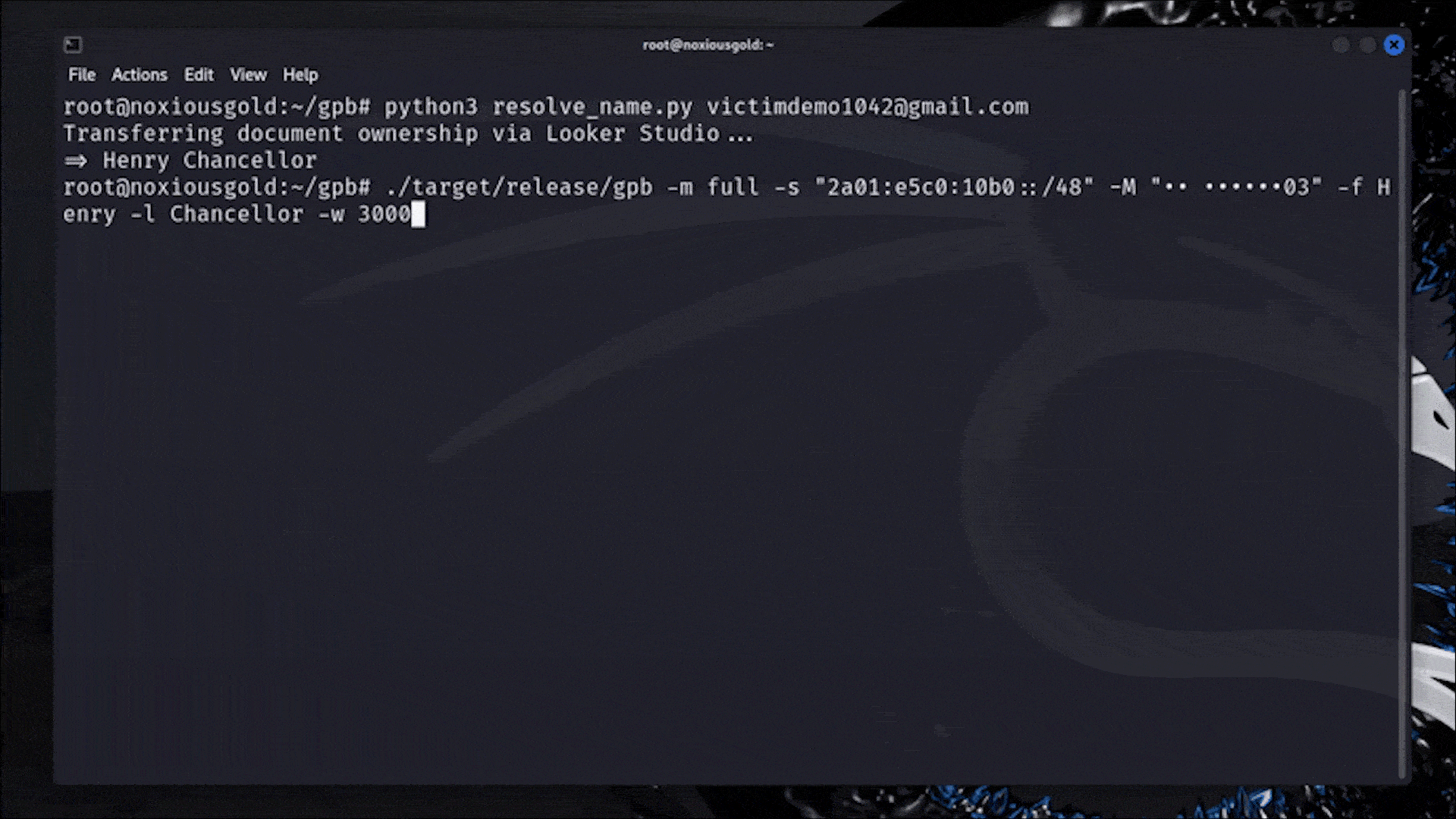
A Researcher Figured Out How to Reveal Any Phone Number Linked to a Google Account
-
Our names, numbers, and home addresses used to be in a book delivered to everyone's door or found stacked in a phone booth on the street. That was normal for generations.
It's funny how much fuckwits can change the course of society and how we can't have nice things.
schrieb am 9. Juni 2025, 18:37 zuletzt editiert vonStill are. I got a phone book delivered a week ago, I shit thee not. Granted I'm on a small island and the book is small too. But like, you can pay to have your number removed from the book. Can you have it removed from this? Not to mention all the 2FA stuff that can be connected to the phone number. Someone clones your number or takes it and suddenly they've got access to a whole lot of your login stuff.
-
Right, but when everyone got phone books, those were only shared locally in the town. It would be pretty hard to figure out someones phone number from across the state/country without the internet unless you knew someone in the town.
You could also pay to be unlisted, which is a luxury long since gone. How cool would it be to make your data 'unlisted' by paying a small monthly fee.
schrieb am 9. Juni 2025, 18:40 zuletzt editiert von obviouslynotbanana@lemmy.world 6. Sept. 2025, 20:44Nevermind
-
Right, but when everyone got phone books, those were only shared locally in the town. It would be pretty hard to figure out someones phone number from across the state/country without the internet unless you knew someone in the town.
You could also pay to be unlisted, which is a luxury long since gone. How cool would it be to make your data 'unlisted' by paying a small monthly fee.
schrieb am 9. Juni 2025, 18:42 zuletzt editiert vonIt would be even cooler if we had a right to privacy
-
God, I hate security "researchers". If I posted an article about how to poison everyone in my neighborhood, I'd be getting a knock on the door. This kind of shit doesn't help anyone. "Oh but the state-funded attackers, remember stuxnet". Fuck off.
schrieb am 9. Juni 2025, 18:42 zuletzt editiert vonI think the method of researching and then informing the affected companies confidentially is a good way to do it but companies often ignore these findings. It has to be publicized somehow to pressure them into fixing the problem.
-
Still are. I got a phone book delivered a week ago, I shit thee not. Granted I'm on a small island and the book is small too. But like, you can pay to have your number removed from the book. Can you have it removed from this? Not to mention all the 2FA stuff that can be connected to the phone number. Someone clones your number or takes it and suddenly they've got access to a whole lot of your login stuff.
schrieb am 9. Juni 2025, 18:42 zuletzt editiert vonMy phone book is smaller than a novel and only has yellow pages these days.
-
God, I hate security "researchers". If I posted an article about how to poison everyone in my neighborhood, I'd be getting a knock on the door. This kind of shit doesn't help anyone. "Oh but the state-funded attackers, remember stuxnet". Fuck off.
schrieb am 9. Juni 2025, 18:46 zuletzt editiert vonWithout researchers like that, someone else would figure it out and use it maliciously without telling anyone. This researcher got Google to close the loophole that the exploit requires before publicly disclosing it.
-
schrieb am 9. Juni 2025, 18:47 zuletzt editiert von
Casually rotating 18,446,744,073,709,551,616 IP addresses to bypass rate limits.
I am not in IT security, but find it fascinating what clever tricks people use to break (into) stuff.
In a better world, we might use this energy for advancing humanity instead of looking how we can hurt each other. (Not saying the author is doing that, just lamenting that ITS is necessary due to hostile actors in this world. )
-
God, I hate security "researchers". If I posted an article about how to poison everyone in my neighborhood, I'd be getting a knock on the door. This kind of shit doesn't help anyone. "Oh but the state-funded attackers, remember stuxnet". Fuck off.
schrieb am 9. Juni 2025, 18:48 zuletzt editiert vonI think it's important for users to know how vulnerable they really are and for providers to have a fire lit under their ass to patch holes. I think it's standard practice to alert providers to these finds early, but I'm guessing a lot of them already knew about the vulnerabilities and often don't give a shit.
Compared to airing this dirty laundry I think the alternatives are potentially worse.
-
Still are. I got a phone book delivered a week ago, I shit thee not. Granted I'm on a small island and the book is small too. But like, you can pay to have your number removed from the book. Can you have it removed from this? Not to mention all the 2FA stuff that can be connected to the phone number. Someone clones your number or takes it and suddenly they've got access to a whole lot of your login stuff.
schrieb am 9. Juni 2025, 18:49 zuletzt editiert vonPay to have it removed! That sounds like blackmail doxing.
-
It would be even cooler if we had a right to privacy
schrieb am 9. Juni 2025, 18:55 zuletzt editiert vonNo doubt, lucky us, we get neither...
-
Right, but when everyone got phone books, those were only shared locally in the town. It would be pretty hard to figure out someones phone number from across the state/country without the internet unless you knew someone in the town.
You could also pay to be unlisted, which is a luxury long since gone. How cool would it be to make your data 'unlisted' by paying a small monthly fee.
schrieb am 9. Juni 2025, 18:55 zuletzt editiert vonPhone books from outside my region were available at the library; that place where they store a consolidated collection of books for just anyone to sign out and use.
-
God, I hate security "researchers". If I posted an article about how to poison everyone in my neighborhood, I'd be getting a knock on the door. This kind of shit doesn't help anyone. "Oh but the state-funded attackers, remember stuxnet". Fuck off.
schrieb am 9. Juni 2025, 18:59 zuletzt editiert vonThis disclosure was from last year and the exploit was patched before the researcher published the findings to the public.
-
Casually rotating 18,446,744,073,709,551,616 IP addresses to bypass rate limits.
I am not in IT security, but find it fascinating what clever tricks people use to break (into) stuff.
In a better world, we might use this energy for advancing humanity instead of looking how we can hurt each other. (Not saying the author is doing that, just lamenting that ITS is necessary due to hostile actors in this world. )
schrieb am 9. Juni 2025, 19:00 zuletzt editiert vonIf you know how to hurt others, you can learn how to prevent that way of hurting others.
-
schrieb am 9. Juni 2025, 19:09 zuletzt editiert von
F. This will be moved to an OSINT tool within a week, and scraped into a darkweb database by next Friday.
-
I set up my GranCentral, now Google Voice, account using a VoIP number from a company that went defunct many years ago. My Google accounts use said Google Voice phone number to validate because GrandCentral wasn't owned by Google back then. I assume this use case is so small, there is no point fixing it. So essentially, my accounts fall into a loop where google leads to google, etc.
heh
schrieb am 9. Juni 2025, 19:30 zuletzt editiert vonI did something of the opposite. I had a Verizon number. I moved it to Google voice. I had a second Google voice number that then became a google fi number. So now I have a Verizon coded google voice number (that my bank accepts etc), and a google fi number that was originally a google voice number. I'm curious how this honestly effects me. My work numbers have never been associated with my personal accounts so there's that.
-
Casually rotating 18,446,744,073,709,551,616 IP addresses to bypass rate limits.
I am not in IT security, but find it fascinating what clever tricks people use to break (into) stuff.
In a better world, we might use this energy for advancing humanity instead of looking how we can hurt each other. (Not saying the author is doing that, just lamenting that ITS is necessary due to hostile actors in this world. )
schrieb am 9. Juni 2025, 19:34 zuletzt editiert vonThose are IPv6 addresses that work a bit differently than IPv4. Most customers only get assigned a single IPv4 address, and even a lot of big data centers only have one or two blocks of 256 addresses. The smallest allocation of IPv6 for a single residential customer is typically a contiguous block of the 18,446,744,073,709,551,616 addresses mentioned.
If Google's security team is even marginally competent, they will recognize those contiguous blocks and treat them as they would a single IPv4 address. Every address in that block has the same prefix, and it's actually easier to track on those prefixes than on the entire address.
-
Casually rotating 18,446,744,073,709,551,616 IP addresses to bypass rate limits.
I am not in IT security, but find it fascinating what clever tricks people use to break (into) stuff.
In a better world, we might use this energy for advancing humanity instead of looking how we can hurt each other. (Not saying the author is doing that, just lamenting that ITS is necessary due to hostile actors in this world. )
schrieb am 9. Juni 2025, 19:38 zuletzt editiert von dan@upvote.au 6. Sept. 2025, 21:42This doesn't really work in real life since IPv6 rate limiting is done per /64 block, not per individual IP address. This is because /64 is the smallest subnet allowed by the IPv6 spec, especially if you want to use features like SLAAC and privacy extensions (which most home users would be using)
SLAAC means that devices on the network can assign their own IPv6. It's like DHCP but is stateless and doesn't need a server.
Privacy extensions means that the IPv6 address is periodically changed to avoid any individual device from being tracked. All devices on an IPv6 network usually have their own public IP, which fixes some things (NAT and port forwarding aren't needed any more) but has potential privacy issues if one device has the same IP for a long time.
-
Ipv6 catching strays
schrieb am 9. Juni 2025, 20:16 zuletzt editiert vonUsually is. Still common among network admins to hear dumb shit like IPv6 being less secure because no NAT.

 ️
️ -
Phone books from outside my region were available at the library; that place where they store a consolidated collection of books for just anyone to sign out and use.
schrieb am 9. Juni 2025, 20:33 zuletzt editiert vonI don't remember that, however it doesn't surprise me at least for a radius around your area. I'd be surprised if they had all of them from all the states
-
F. This will be moved to an OSINT tool within a week, and scraped into a darkweb database by next Friday.
schrieb am 9. Juni 2025, 20:48 zuletzt editiert vonI think you missed the part at the very end of the page that showed the timeline of them reporting the vulnerability back in April, being rewarded for finding the vulnerability, the vulnerability being patched in May, and being allowed to publicize the vulnerability as of today.
-
(Edited title, see details for original) Here's why you're getting enshittified...
Technology54 vor 13 Tagenvor 14 Tagen 1
1
-
-
-
Scientists reportedly hiding AI text prompts in academic papers to receive positive peer reviews
Technology 14. Juli 2025, 07:16 1
1
-
A chemical industry lobbyist is attempting to use AI to amplify doubts about the dangers of pollutants
Technology 28. Juni 2025, 13:19 1
1
-
Samsung is desperate to compete on chips. Workers say it comes at a cost.
Technology 16. Juni 2025, 10:40 1
1
-
-