NGINX & Webmin
-
Kurz mal was Testen
 System ist ein Buster-minimal vom Kamil. Auf Debian 10.1 aktualisiert.
System ist ein Buster-minimal vom Kamil. Auf Debian 10.1 aktualisiert.Installation Webmin
NGINX Module

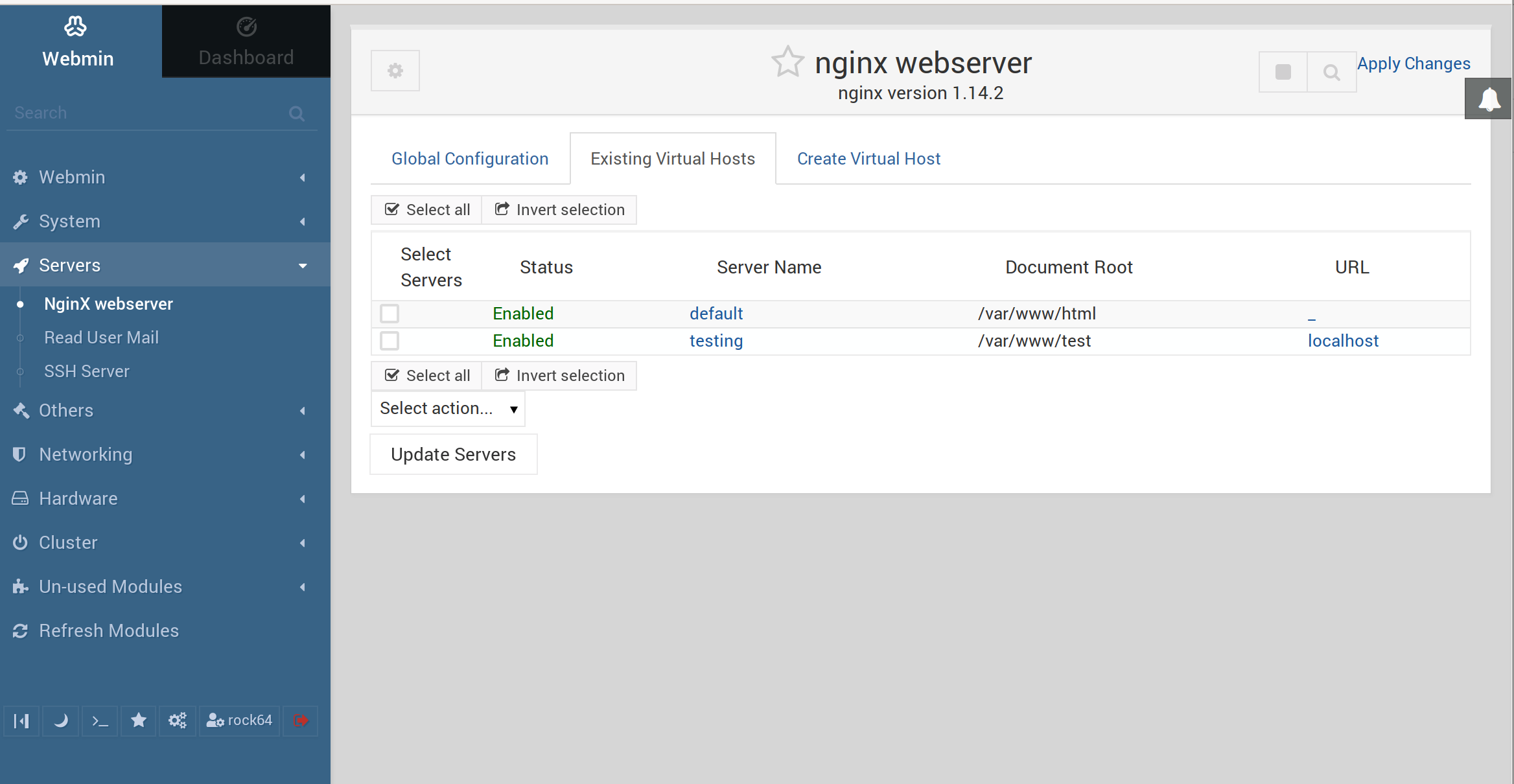
Using Webmin Module to Manage nginx Sites on EasyEngine •
Using Webmin Module to Manage nginx Sites on EasyEngine and other systems for WordPress or any CMS to easily modify and enable or disable virtual hosts

WP Bullet Guides (guides.wp-bullet.com)

Nginx Webmin Module | Justin D Hoffman
This project aims to give a user interface to those wishing to update nginx settings through webmin and to use nginx to server up some pages. Sometimes it's faster to not use the command line to fix everything or set up a new site. With this webmin module you'll be able to work on your nginx server from webmin.

(www.justindhoffman.com)
Danach bekam ich eine 500er Fehlermeldung. Irgendwas mit
perl missing HTML::EntitiesDanach
rock64@rockpro64:~$ sudo cpan perl: warning: Setting locale failed. perl: warning: Please check that your locale settings: LANGUAGE = (unset), LC_ALL = (unset), LANG = "de_DE.UTF-8" are supported and installed on your system. perl: warning: Falling back to the standard locale ("C"). Loading internal logger. Log::Log4perl recommended for better logging CPAN.pm requires configuration, but most of it can be done automatically. If you answer 'no' below, you will enter an interactive dialog for each configuration option instead. Would you like to configure as much as possible automatically? [yes] yes Autoconfiguration complete. commit: wrote '/root/.cpan/CPAN/MyConfig.pm' You can re-run configuration any time with 'o conf init' in the CPAN shell Terminal does not support AddHistory. cpan shell -- CPAN exploration and modules installation (v2.20) Enter 'h' for help. cpan[1]> install HTML::Entities Fetching with HTTP::Tiny: http://www.cpan.org/authors/01mailrc.txt.gz Reading '/root/.cpan/sources/authors/01mailrc.txt.gz' ............................................................................DONE [...........gekürzt...............]Danach läuft ein riesiges Script und ich habe keine Ahnung was das so alles veranstaltet.
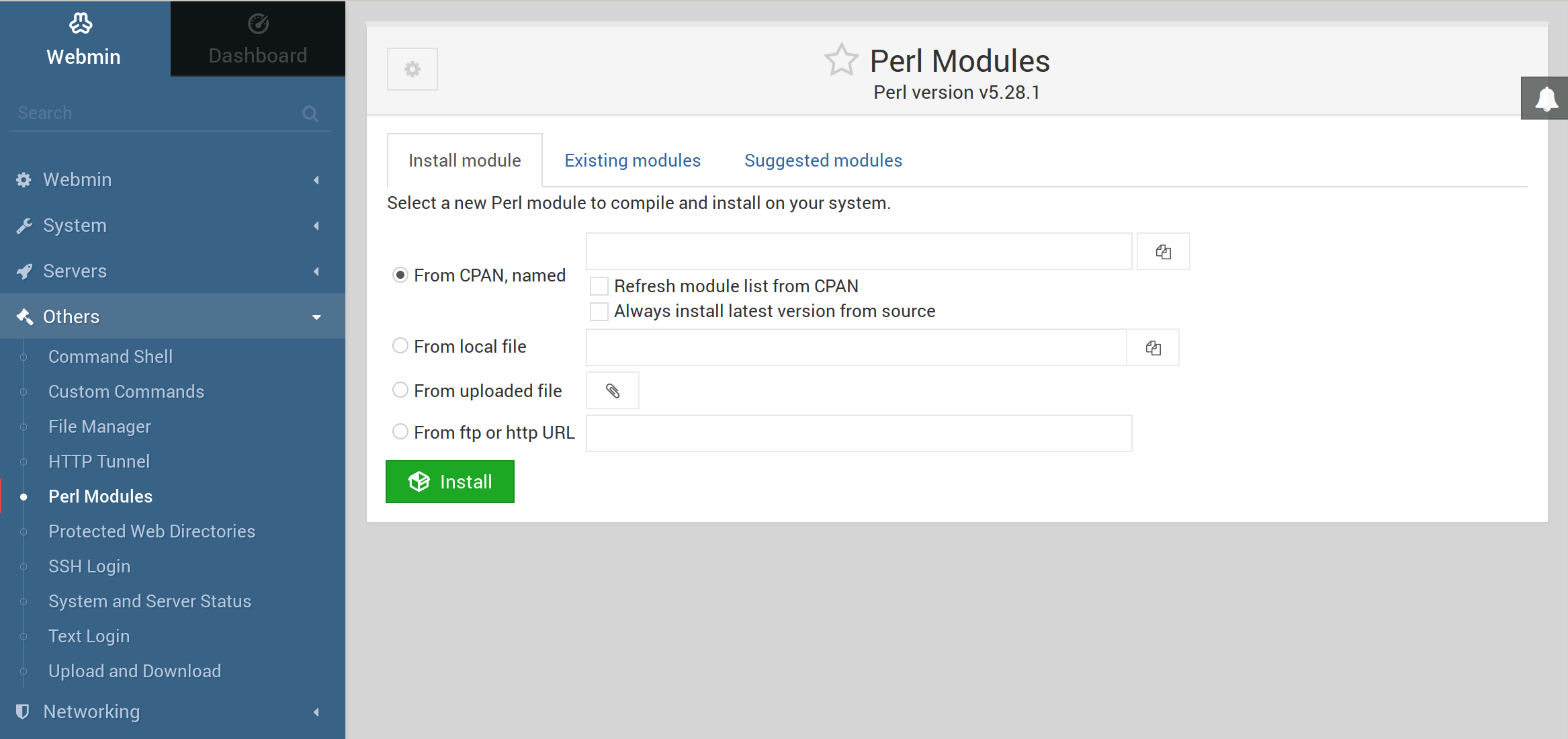
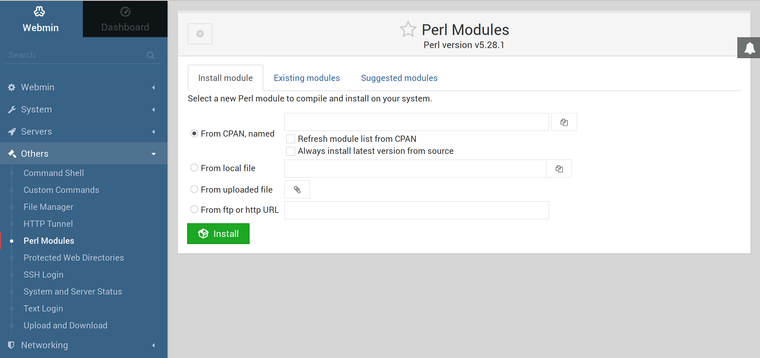
Nach einer Neuinstallation entdeckt, das man die Perl Module auch über das Webinterface installieren kann.
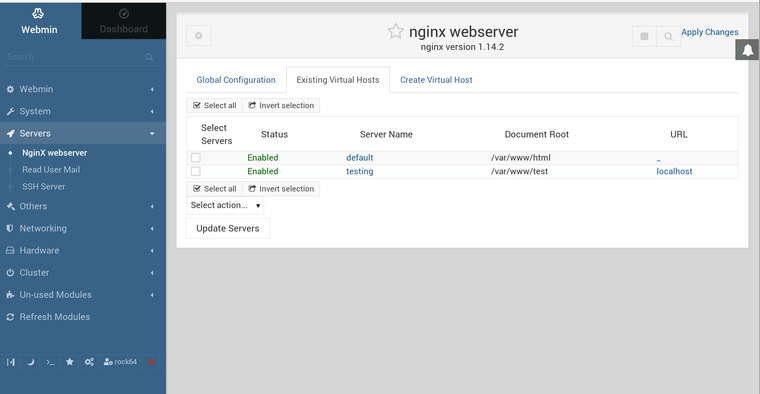
Danach kann man den NGINX über Webmin administrieren.
-
Danach die Firewalld in Betrieb nehmen

sudo apt install firewalldEs werden Standard Rules geladen, die einem aus dem Webmin Interface rauswerfen.
rock64@rockpro64:/var/www$ sudo iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED ACCEPT all -- anywhere anywhere INPUT_direct all -- anywhere anywhere INPUT_ZONES_SOURCE all -- anywhere anywhere INPUT_ZONES all -- anywhere anywhere DROP all -- anywhere anywhere ctstate INVALID REJECT all -- anywhere anywhere reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED ACCEPT all -- anywhere anywhere FORWARD_direct all -- anywhere anywhere FORWARD_IN_ZONES_SOURCE all -- anywhere anywhere FORWARD_IN_ZONES all -- anywhere anywhere FORWARD_OUT_ZONES_SOURCE all -- anywhere anywhere FORWARD_OUT_ZONES all -- anywhere anywhere DROP all -- anywhere anywhere ctstate INVALID REJECT all -- anywhere anywhere reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) target prot opt source destination OUTPUT_direct all -- anywhere anywhere Chain INPUT_direct (1 references) target prot opt source destination Chain INPUT_ZONES_SOURCE (1 references) target prot opt source destination Chain INPUT_ZONES (1 references) target prot opt source destination IN_public all -- anywhere anywhere [goto] Chain FORWARD_direct (1 references) target prot opt source destination Chain FORWARD_IN_ZONES_SOURCE (1 references) target prot opt source destination Chain FORWARD_IN_ZONES (1 references) target prot opt source destination FWDI_public all -- anywhere anywhere [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) target prot opt source destination Chain FORWARD_OUT_ZONES (1 references) target prot opt source destination FWDO_public all -- anywhere anywhere [goto] Chain OUTPUT_direct (1 references) target prot opt source destination Chain IN_public (1 references) target prot opt source destination IN_public_log all -- anywhere anywhere IN_public_deny all -- anywhere anywhere IN_public_allow all -- anywhere anywhere ACCEPT icmp -- anywhere anywhere Chain IN_public_log (1 references) target prot opt source destination Chain IN_public_deny (1 references) target prot opt source destination Chain IN_public_allow (1 references) target prot opt source destination ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW,UNTRACKED Chain FWDI_public (1 references) target prot opt source destination FWDI_public_log all -- anywhere anywhere FWDI_public_deny all -- anywhere anywhere FWDI_public_allow all -- anywhere anywhere ACCEPT icmp -- anywhere anywhere Chain FWDI_public_log (1 references) target prot opt source destination Chain FWDI_public_deny (1 references) target prot opt source destination Chain FWDI_public_allow (1 references) target prot opt source destination Chain FWDO_public (1 references) target prot opt source destination FWDO_public_log all -- anywhere anywhere FWDO_public_deny all -- anywhere anywhere FWDO_public_allow all -- anywhere anywhere Chain FWDO_public_log (1 references) target prot opt source destination Chain FWDO_public_deny (1 references) target prot opt source destination Chain FWDO_public_allow (1 references) target prot opt source destinationLösung: https://doxfer.webmin.com/Webmin/FirewallD
Ein
rock64@rockpro64:/var/www$ sudo firewall-cmd --reload Error: COMMAND_FAILED: '/usr/sbin/ebtables-restore --noflush' failed: line 3: CHAIN_USER_DEL failed (Device or resource busy): chain PREROUTING_direct line 3: CHAIN_USER_DEL failed (Device or resource busy): chain POSTROUTING_direct line 3: CHAIN_USER_DEL failed (Device or resource busy): chain OUTPUT_direct line 7: CHAIN_USER_DEL failed (Device or resource busy): chain INPUT_direct line 7: CHAIN_USER_DEL failed (Device or resource busy): chain OUTPUT_direct line 7: CHAIN_USER_DEL failed (Device or resource busy): chain FORWARD_direct.brachte aber nur Probleme!?
Ein Reboot löste das Problem. Aber, das ist ein wenig unbefriedigend, da muss ich nochmal ran....
-
Das was da oben steht über Firewalld, ganz schnell vergessen. Das brauchen wir nicht, hat auch nur Probleme gemacht....
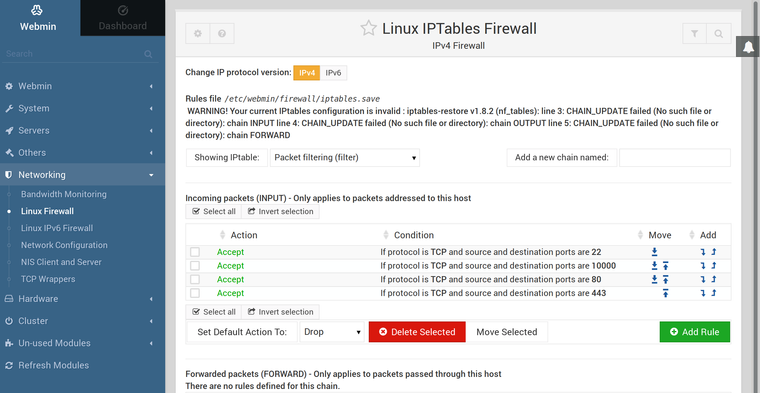
Man kann ganz normal mit iptables arbeiten, man sollte schon mal eine Firewall konfiguriert haben, das macht es etwas einfacher.
Kurzer Test, ob das so klappt wie erwartet.
frank@debian:~$ nmap 192.168.3.6 Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-13 19:57 CEST Nmap scan report for 192.168.3.6 Host is up (0.0011s latency). Not shown: 996 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 443/tcp closed https 10000/tcp open snet-sensor-mgmtDas hier sind aktuell die Regeln.
root@rockpro64:~# iptables-legacy -L Chain INPUT (policy DROP) target prot opt source destination ACCEPT tcp -- anywhere anywhere tcp multiport ports ssh ACCEPT tcp -- anywhere anywhere tcp multiport ports webmin ACCEPT tcp -- anywhere anywhere tcp multiport ports http ACCEPT tcp -- anywhere anywhere tcp multiport ports https Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destinationWenn ich das so die ganze Zeit teste, dann zweifel ich immer daran, ob solche Tools(Webmin) irgend einen Vorteil haben!? Mir macht das mittlerweile mehr Arbeit, als wenn ich das alles schnell eben auf der Konsole erledige. Vielleicht bin ich auch nur mittlerweile zu weit weg, von grafischen UI. Ich gebe dem Webmin aber noch ein paar Tage, gibt noch ein paar Sachen zu entdecken.
-
-
-
-
-
-
NodeBB & ads.txt
Verschoben NGINX -
-