Robot performs first realistic surgery without human help: System trained on videos of surgeries performs like an expert surgeon
-
Naturally as this kind of thing moves into use on actual people it will be used on the wealthiest and most connected among us in equal measure to us lowly plebs right.....right?
Are you kidding!? It'll be rolled out to poor people first! (gotta iron out the last of the bugs somehow)
-
I'd bet on at least twenty years before it's in general use, since this is a radical change and it makes sense to be cautious about new technology in medicine. Initial clinical trials for some common, simple surgeries within ten years, though.
This is one of those cases where an algorithm carefully trained on only relevant data can have value. It isn't the same as feeding an LLM the unfiltered Internet and then expecting it to learn only from the non-crazy parts.
This is one of those cases where an algorithm carefully trained on only relevant data can have value.
Hopefully more people learn that this is the important part.
It becomes nonsense when you just feed it everything and the kitchen sink. A well trained model works.
-
Would it be able to handle a sudden power outage? A fire alarm going off?
What happens to an ecmo machine during a power outage or fire alarm?
The idea should be to augment healthcare professionals with tools they can use. The hospital will need to have contingencies in place. I agree if that your point is that we can’t replace people with machines. But we can increase effectiveness with them.
-
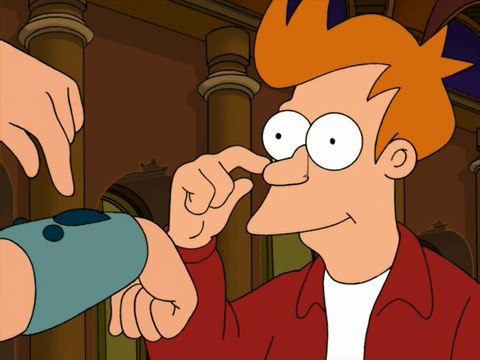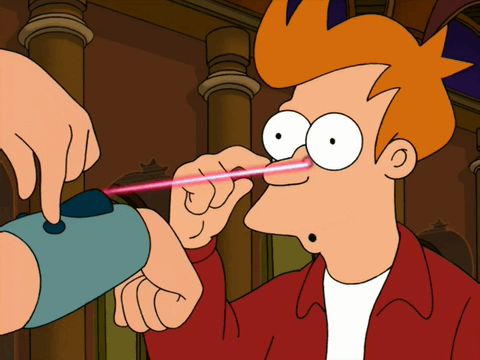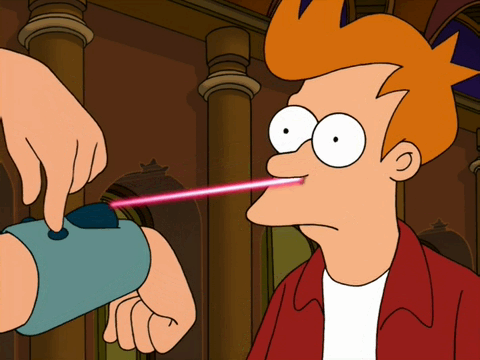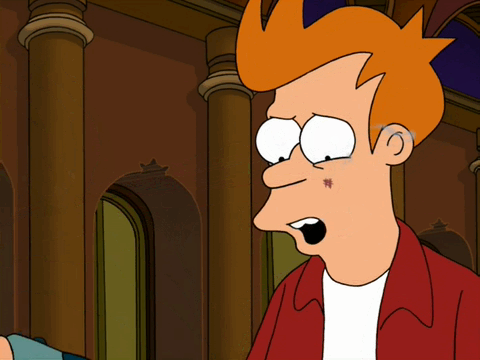
A robot trained on videos of surgeries performed a lengthy phase of a gallbladder removal without human help. The robot operated for the first time on a lifelike patient, and during the operation, responded to and learned from voice commands from the team—like a novice surgeon working with a mentor.
The robot performed unflappably across trials and with the expertise of a skilled human surgeon, even during unexpected scenarios typical in real life medical emergencies.
So are we fully abandoning reason based robots?
Is the future gonna just be things that guess but just keep getting better at guessing?
I’m disappointed in the future.
-
A robot trained on videos of surgeries performed a lengthy phase of a gallbladder removal without human help. The robot operated for the first time on a lifelike patient, and during the operation, responded to and learned from voice commands from the team—like a novice surgeon working with a mentor.
The robot performed unflappably across trials and with the expertise of a skilled human surgeon, even during unexpected scenarios typical in real life medical emergencies.
without human help
...
responded to and learned from voice commands from the team
🤨

-
So are we fully abandoning reason based robots?
Is the future gonna just be things that guess but just keep getting better at guessing?
I’m disappointed in the future.
That’s all people are too, though.
-
without human help
...
responded to and learned from voice commands from the team
🤨

They should have specified "without physical human help."
-
I want that thing where a light "paints" over wounds and they heal.
-
So are we fully abandoning reason based robots?
Is the future gonna just be things that guess but just keep getting better at guessing?
I’m disappointed in the future.
Reasoning is just informed guessing.
-
Are you kidding!? It'll be rolled out to poor people first! (gotta iron out the last of the bugs somehow)
You really don't understand modern medical bullshit. The rich will be all over this, just like AI, Just like NFTs just like every bullshit thing that comes up they get roped into by a flashy salesman
-
A robot trained on videos of surgeries performed a lengthy phase of a gallbladder removal without human help. The robot operated for the first time on a lifelike patient, and during the operation, responded to and learned from voice commands from the team—like a novice surgeon working with a mentor.
The robot performed unflappably across trials and with the expertise of a skilled human surgeon, even during unexpected scenarios typical in real life medical emergencies.
Okay but why? No thank you.
-
Would it be able to handle a sudden power outage? A fire alarm going off?
As well as a human, and without fucking up because of stress.
Also my guess is these would be monitored by trained professionals. -
Reasoning is just informed guessing.
-
Right I'm sure a bunch of arm chair docs on lemme are totally more knowledgeable and have more understanding of all this and their needed procedures than actual licensed doctors.
More than the doctors? No, absolutely not.
More than the bean counters who want to replace these doctors with unsupervised robots? I'm a lot more confident on that one.
-
know what? let's just skip the middleman and have the CEO undergo the same operation. you know like the taser company that tasers their employees.
can't have trust in a product unless you use the product.
I understand what you are saying is intended as „if they trust their product they should use it themselves“ and I agree with that
I do think that undergoing an operation that a person doesnt need isnt ethical however
-
You really don't understand modern medical bullshit. The rich will be all over this, just like AI, Just like NFTs just like every bullshit thing that comes up they get roped into by a flashy salesman
Oh yeah, I've been successfully propagandized into thinking rich people became rich through merit, I forgot how many of them are complete morons XD
Thanks for reminding me
-
I understand what you are saying is intended as „if they trust their product they should use it themselves“ and I agree with that
I do think that undergoing an operation that a person doesnt need isnt ethical however
who said they won't need it

-
without human help
...
responded to and learned from voice commands from the team
🤨

I have seen enough ER to know that operating theatre staff work as a team. So I consider this would be a good thing.
-
And that's all for analyzing statements. You can't just do that to some words and discover objective truth out of nowhere, so I'm not sure what you think you're accomplishing here. What you're linking is more analogous to the code that underlies an AI(if/while loops and whatnot). Reasoning is closer to the scientific method of forming a hypothesis and whatnot than anything you linked.
You basically just pointed out that there's a math system for logic. Neat.
-
A robot trained on videos of surgeries performed a lengthy phase of a gallbladder removal without human help. The robot operated for the first time on a lifelike patient, and during the operation, responded to and learned from voice commands from the team—like a novice surgeon working with a mentor.
The robot performed unflappably across trials and with the expertise of a skilled human surgeon, even during unexpected scenarios typical in real life medical emergencies.
so this helps with costs right? right? 🥺
 🤨
🤨







