UK households could face VPN 'ban' after use skyrockets following Online Safety Bill
-
this is obviously such a dumpster fire that I can't help but wonder, "When will they realize how dumb this is and back out of it?"
then i remember that Brexit happened
fuckin stubbornness is a national identity for you blokes innit
We didn't have a referendum on this though, and if we had done I don't think it would have passed
-
Prominent backbench MP Sarah Champion launched a campaign against VPNs previously, saying: “My new clause 54 would require the Secretary of State to publish, within six months of the Bill’s passage, a report on the effect of VPN use on Ofcom’s ability to enforce the requirements under clause 112.
"If VPNs cause significant issues, the Government must identify those issues and find solutions, rather than avoiding difficult problems.” And the Labour Party said there were “gaps” in the bill that needed to be amended.
People are "at risk"... of what? What a terrible article to not even clarify what the risk is. Because it sounds to me like the government is who put those people at risk by making them go look for solutions to a draconian policy.
-
Yeah, businesses will not accept this. Remote work and remote connections rely on VPN for ALL KINDS OF SHIT. If you must adhere to some kinds of government compliance, it is even MANDATED BY THE FUCKING GOVERNMENT. Explain to me how the hell that is going to just poof and not cause all kinds of problems.
Individual customer VPN providers get banned, corporate VPN providers not banned. It's quite simple really.
Or are you expecting the average Joe to spin up his own VPN server?
-
We didn't have a referendum on this though, and if we had done I don't think it would have passed
Same was said during Brexit.
-
Convert churches into museums for art and displaying the horrors of religion
Not all of them have pretty art. Just turn the boring looking ones into secular club houses or even just regular housing.
True, and yes, please
-
And how do they update that IP list? Manually?
If you set up your own overseas server, it's gonna be ok for a few days for sure. But they update the block list automatically so people had to e.g. use CloudFlare websocket as a jump host to avoid switching providers every other month. Of cos CF is mostly blocked these days too so it's probably just easier to offload the work to those VPN operators you mentioned.Universities are a different matter. They use Edu network and there used to be no censorship at all in Edu IPv6. Nowadays it's still relatively easy for them to get exemptions for their labs and whatnot.
I don't know how they update their IP list. My university is an American university which I believe has no ties to China, but I can't say for sure. According to friends who use the clandestine OpenVPN services, they pay about 20 CNY a month and every month they are issued a new OVPN configuration file. Only occasionally do their servers get blocked before this, and then they have to issue new config files to everyone.
As for myself, I have been to China two times using the OpenVPN server that I deployed on a US-based VPS I rented from a German hosting provider. Each trip lasted about one month. So far, the IP has not been blocked. The government's philosophy regarding the firewall and VPNs seems to be "make it as annoying as possible for the average uninformed layperson to bypass and go after people selling illegal VPNs, but otherwise, we don't give a shit". I do not sell access to my VPN to anyone else. It is strictly for my own use.
Both times I was there, the firewall didn't apply to cellular data because they do not apply the firewall to holders of foreign SIM cards using their cellular service. I purchased a SIM from a Hong Kong carrier (SoSim) with a few gigabytes of data in both Hong Kong and mainland China for 100 HKD. The firewall doesn't apply within Hong Kong. It worked fine, though I do note that surveillance laws meant that I had to upload my passport to activate the service. I'm not a big fan of that, so I kept the VPN connected at all times, though normally-blocked websites did indeed work on cellular data even without the VPN. I checked on my cell phone's settings, and I know it connects to China Mobile towers when in mainland China. Note that China Mobile is owned by the Chinese state.
I also confirmed that it doesn't apply the firewall when I have my T-Mobile (my US cell carrier) SIM in there. My carrier provides unlimited worldwide roaming at 2G speeds but I can confirm that it also connects to China Mobile towers and I could successfully access Wikipedia, a blocked site, without the VPN.
-
Prominent backbench MP Sarah Champion launched a campaign against VPNs previously, saying: “My new clause 54 would require the Secretary of State to publish, within six months of the Bill’s passage, a report on the effect of VPN use on Ofcom’s ability to enforce the requirements under clause 112.
"If VPNs cause significant issues, the Government must identify those issues and find solutions, rather than avoiding difficult problems.” And the Labour Party said there were “gaps” in the bill that needed to be amended.
China 1.5
-
this is obviously such a dumpster fire that I can't help but wonder, "When will they realize how dumb this is and back out of it?"
then i remember that Brexit happened
fuckin stubbornness is a national identity for you blokes innit
Don't forget the raging alcoholism
-
Proxy is a step below VPN since it doesn't tunnelise data.
Anti-detect browsers. Do you mean Tor? It's a decent solution, albeit the slowest one.
What people use to bypass the great Chinese firewall is VPN with VLESS protocols. Unlike usual VPN protocols, those are specifically made to bypass censorship.
no not TOr, there are better proxies than what you are thinking, no not tor browsers.
-
Same was said during Brexit.
We very much did have a referendum on brexit though
-
We very much did have a referendum on brexit though
What I meant was during the Brexit referendum most people were saying it wouldn't pass. In other words, if there was a referendum for this it probably WOULD pass since it's really easy to influence people through media.
-
This makes me feel like they were in a bind here. The so called "online safety bill" was a tory concoction that took years to pass through the courts because of how invasive it is and how anyone could easily bypass it.
If labour want to stop it, they'll be accused of not wanting to protect children.
Whatever anyone thinks of labour, I'd ask people to ask themselves, if you were in that position, what option do they have other than to let it play out as the spectacular failure it was always going to be and making sure everyone knows who's fault that was afterwards?
No. They could put it into a review and quietly shitcan this. It's not particularly popular. They just want to say they're protecting kids.
They're spineless and Keir is an authoritarian.
-
That's a problem is for ISPs and content providers to figure out. I don't see why the government has to care other than laying out the ground rules - you must offer and implement a parental filter for people who want it for free as part of your service. If ISPs have to do deep packet inspection and proxy certs for protected devices / accounts then that's what they'll have to do.
As far as the government is concerned it's not their problem. They've said what should happen and providing the choice without being assholes to people over 18 who are exercising their rights to use the internet as they see fit.
That’s a problem is for ISPs and content providers to figure out
No, there are very good technical reasons why this approach can't work.
ISPs ... deep packet inspection
There is no deep packet inspection on properly encrypted TLS connections. I know TLS termination and interception and recertifying with custom certificates is a thing, but even if it were feasible to implement this on millions of client computers that you don't own, it is an absolutely god awful idea for a million reasons and much worse for privacy and security than the age-gate problem you're trying to work around.
-
I though the UK was a Western democracy. What the hell are you guys doing over there?
Lol. Democracy.
Democracies don't care about their citizens privacy. Just the optics of getting spied on citizens.
-
That’s a problem is for ISPs and content providers to figure out
No, there are very good technical reasons why this approach can't work.
ISPs ... deep packet inspection
There is no deep packet inspection on properly encrypted TLS connections. I know TLS termination and interception and recertifying with custom certificates is a thing, but even if it were feasible to implement this on millions of client computers that you don't own, it is an absolutely god awful idea for a million reasons and much worse for privacy and security than the age-gate problem you're trying to work around.
Actually it can be done and is being done. Software like Fortigate Firewall can do deep packet inspection on encrypted connections by replacing certs with their own and doing man in the middle inspection. It requires the browser has a root CA cert that trusts the certs issued by the proxy but that's about it. Filtering software could onboard a new device where the root cert could be installed.
And if Fortigate can do it then any filtering software can too. e.g. a kid uses their filtered device to go to reddit.com, the filter software substitutes reddit's cert for their own and proxies the connection. Then it looks at the paths to see if the kid is visiting an innocuous group or an 18+ group. So basic filtering rules could be:
- If domain is entirely blocked, just block it.
- If domain hosts mixed content, deep packet inspection & block if necessary
- If domain is innocuous allow it through
This is eminently possible for an ISP to implement and do so in a way that it ONLY happens when a user opts into it on a registered device while leaving everything open if they did not opt into it.
And like I said this is an ISP problem to figure out. The government could have set the rules and walked away. And as a solution it would be far more simple that requiring every website to implement age verification.
-
@arc99 @SpaceCadet thats basically allowing the Government to force ISP to build a solution which is able to sensor every content. Sorry there is alot of reasons why you should be against it.
Deep packet inspection already happens on encrypted traffic (Fortigate Firewall) so it's eminently possible for filtering software to do the same.
-
Attached below is a Wireshark trace I obtained by sniffing my own network traffic.

I want to draw your attention to this part in particular:
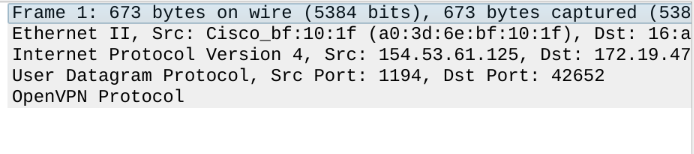
Underneath "User Datagram Protocol", you can see the words "OpenVPN Protocol". So anyone who sniffs my traffic on the wire can see exactly the same thing that I can. While they can't read the contents of the payload, they can tell that it's OpenVPN traffic because the headers are not encrypted. So if a router wanted to block OpenVPN traffic, all they would have to do is drop this packet. It's a similar story for Wireguard packets. An attacker can read the unencrypted headers and learn
- The size of the transmission
- The source and destination IP addresses by reading the IP header
- The source and destination ports numbers by reading the TCP or UDP headers
- The underlying layers, up until the point it hits an encrypted protocol (such as OpenVPN, TLS, or SSH)
You're using the default port though, are you not? If the source port were not 1194, a port associated with openvpn, would wireshark still identify this as openvpn traffic?
-
Actually it can be done and is being done. Software like Fortigate Firewall can do deep packet inspection on encrypted connections by replacing certs with their own and doing man in the middle inspection. It requires the browser has a root CA cert that trusts the certs issued by the proxy but that's about it. Filtering software could onboard a new device where the root cert could be installed.
And if Fortigate can do it then any filtering software can too. e.g. a kid uses their filtered device to go to reddit.com, the filter software substitutes reddit's cert for their own and proxies the connection. Then it looks at the paths to see if the kid is visiting an innocuous group or an 18+ group. So basic filtering rules could be:
- If domain is entirely blocked, just block it.
- If domain hosts mixed content, deep packet inspection & block if necessary
- If domain is innocuous allow it through
This is eminently possible for an ISP to implement and do so in a way that it ONLY happens when a user opts into it on a registered device while leaving everything open if they did not opt into it.
And like I said this is an ISP problem to figure out. The government could have set the rules and walked away. And as a solution it would be far more simple that requiring every website to implement age verification.
I know how it works, so spare me the explanation. It's not that as easy as you make it out to be. OS and browser companies are actively fighthing "rogue" root CAs and making it harder and harder to use custom CAs, especially on mobile devices.
And for good reason, because by accepting a rogue root CA that's not your own, you're basically undermining the whole trust system that SSL is based on and surrendering all your online privacy and security to the government and your ISP. Whoever has control over that custom root CA has the keys to your online life.
Rolling such a system out countrywide is utter madness.
-
What I meant was during the Brexit referendum most people were saying it wouldn't pass. In other words, if there was a referendum for this it probably WOULD pass since it's really easy to influence people through media.
I get what you mean, for it to be comparable I think we'd need a "should there be legislation to protect kids on the Internet" referendum and then this is the implementation and everyone hates it...
-
I know how it works, so spare me the explanation. It's not that as easy as you make it out to be. OS and browser companies are actively fighthing "rogue" root CAs and making it harder and harder to use custom CAs, especially on mobile devices.
And for good reason, because by accepting a rogue root CA that's not your own, you're basically undermining the whole trust system that SSL is based on and surrendering all your online privacy and security to the government and your ISP. Whoever has control over that custom root CA has the keys to your online life.
Rolling such a system out countrywide is utter madness.
You obviously didn't know how it works if I had to explain it was already possible. And I am not aware of any mobile device that prevents you installing a new root CA.
And it isn't "madness", it's a completely workable way to offer filtering for people who want it for kids and have no filtering or censorship for anybody else. It is a vastly better option than onerously demanding adults provide their identity to random and potentially adult themed websites where they could be victims of identity theft or extortion







