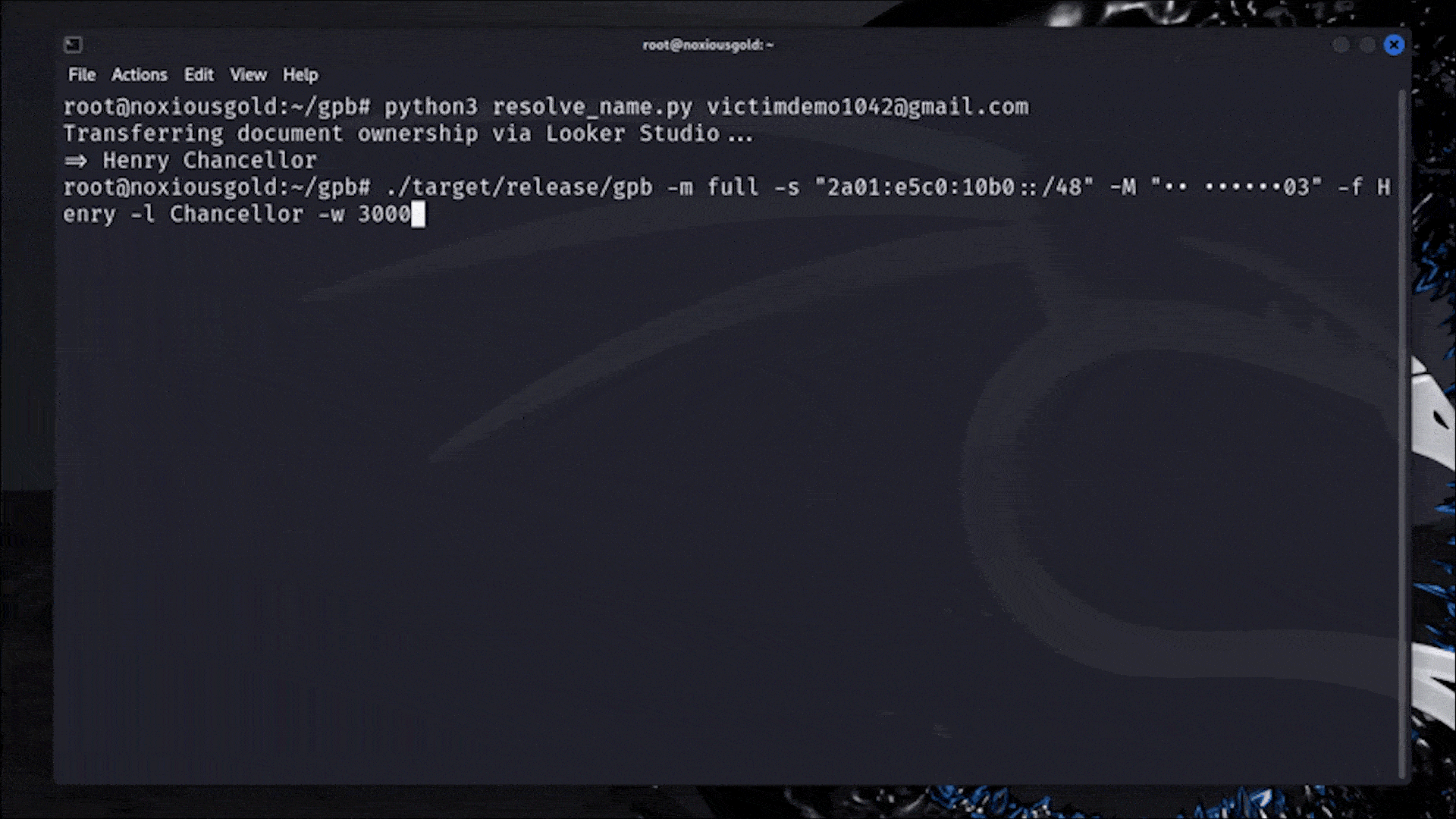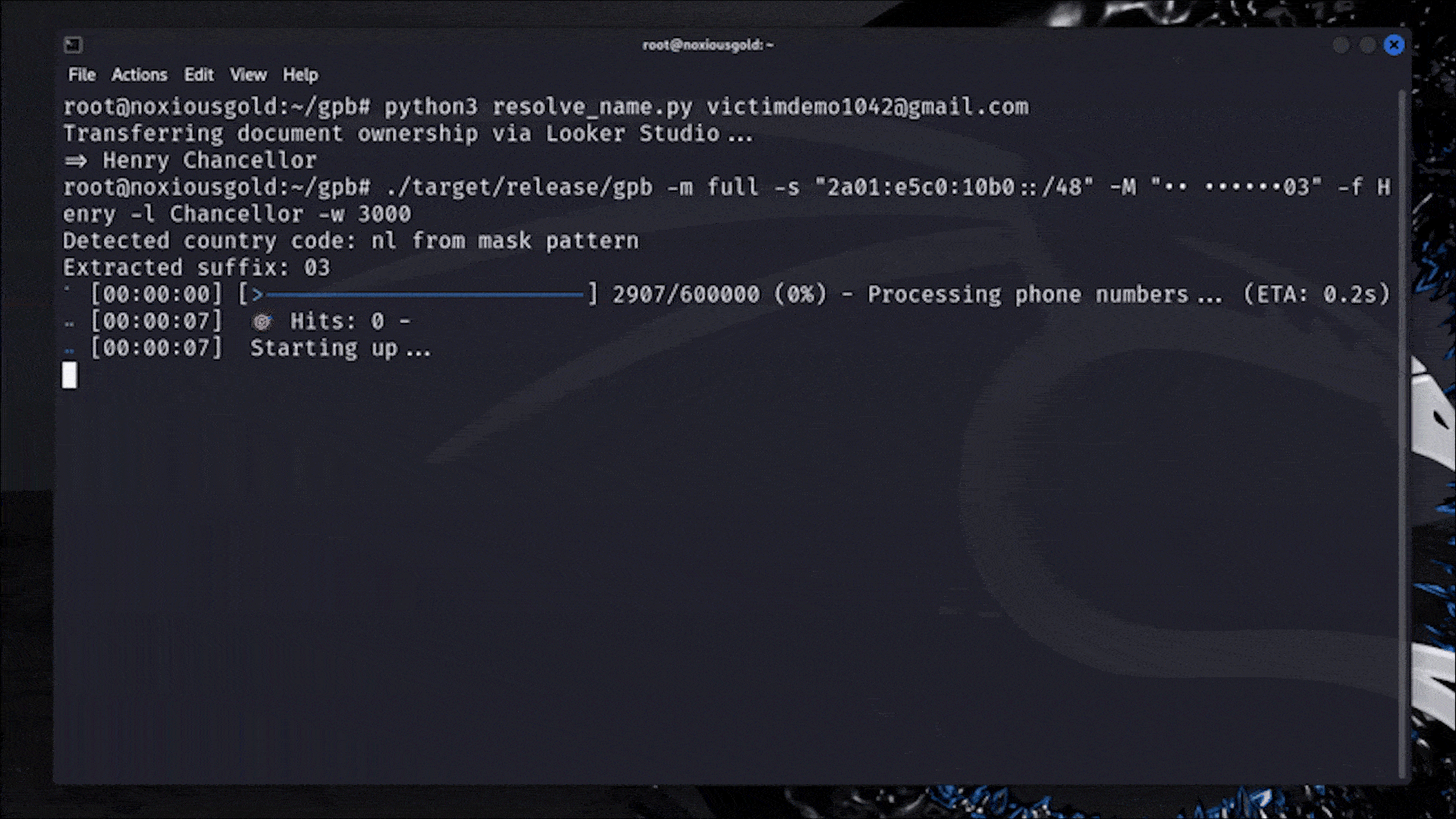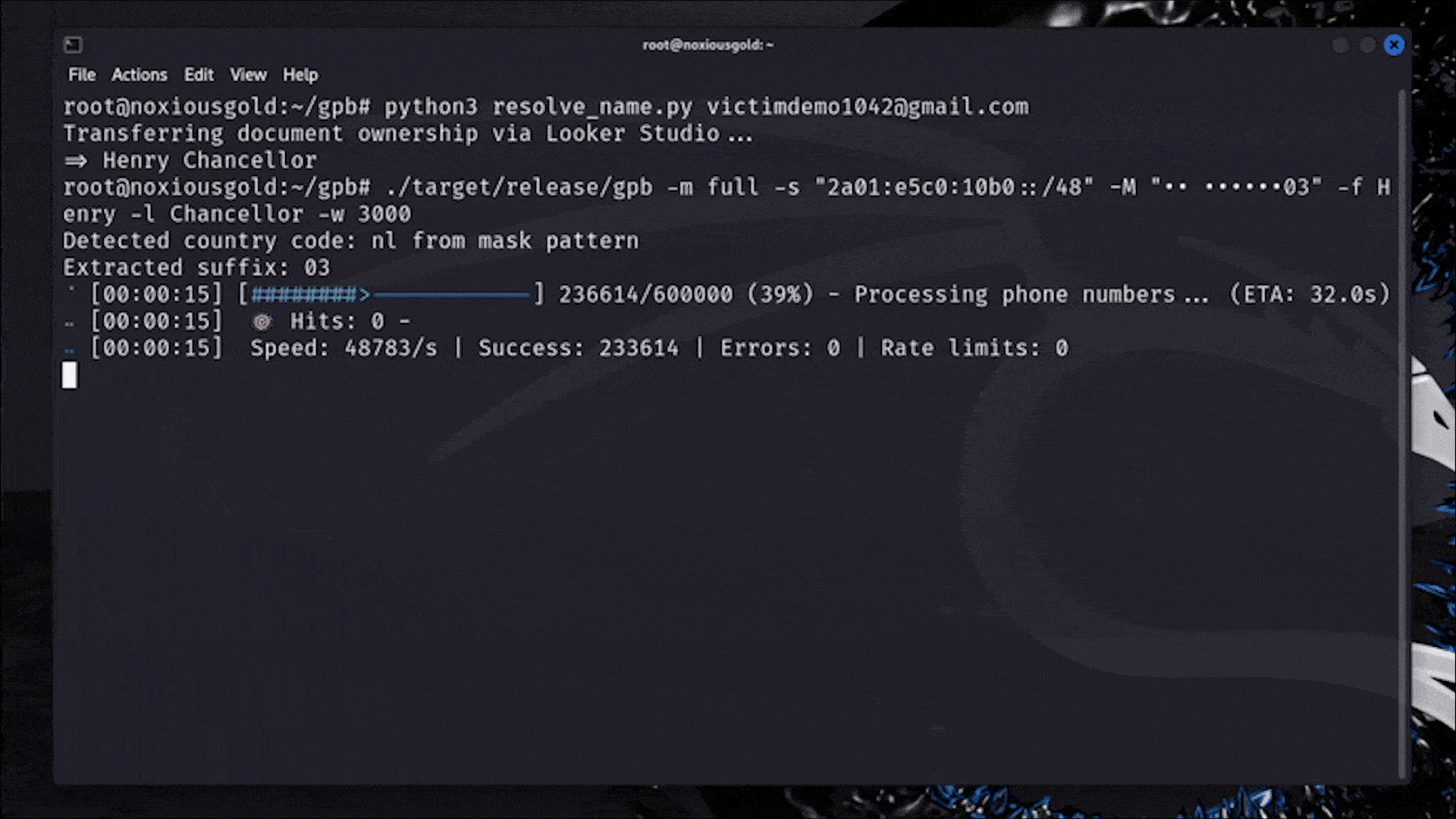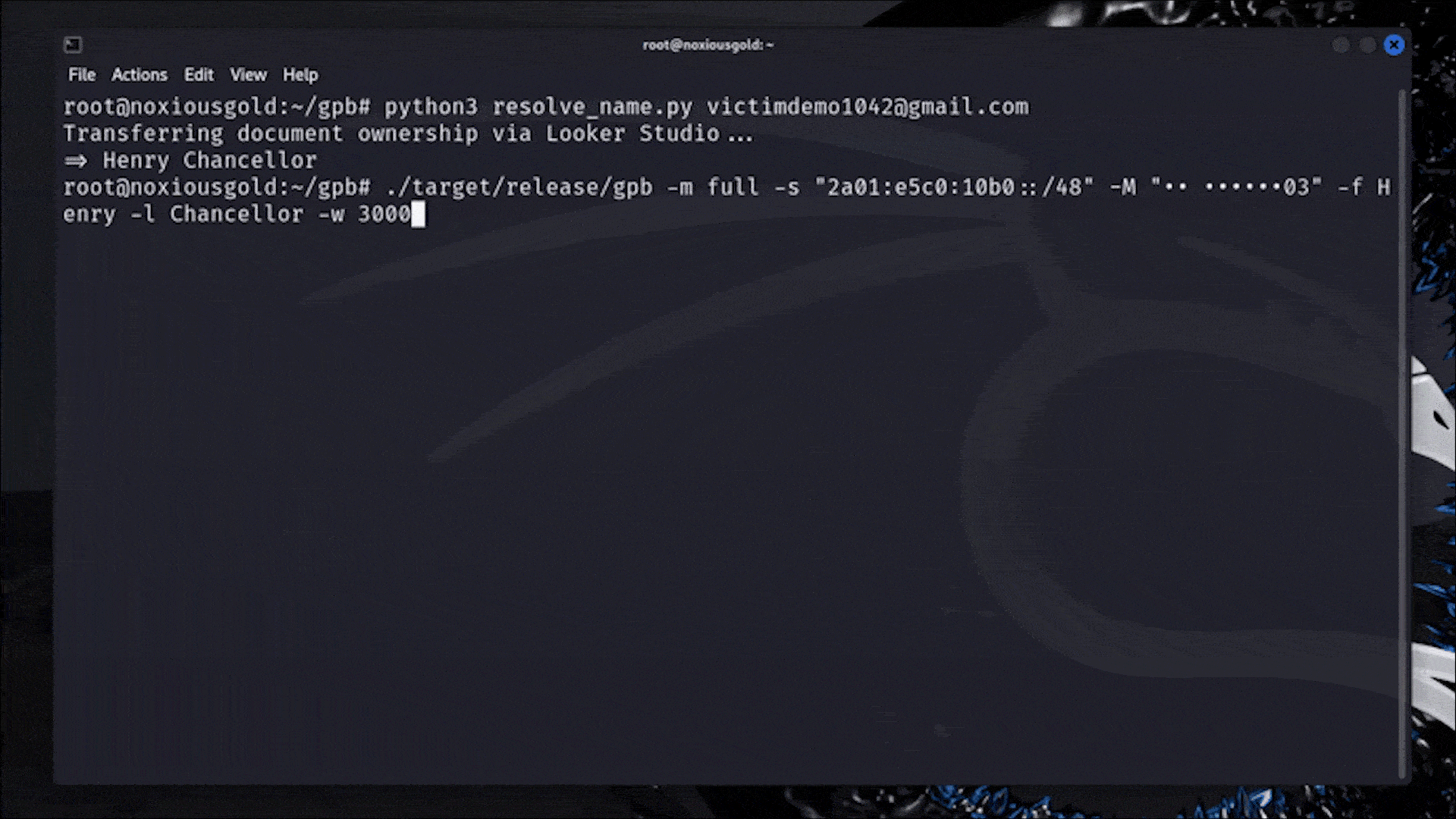
A Researcher Figured Out How to Reveal Any Phone Number Linked to a Google Account
-
-
Most service providers like Vultr provide /64 ip ranges, which provide us with 18,446,744,073,709,551,616 addresses. In theory, we could use IPv6 and rotate the IP address we use for every request, bypassing this ratelimit.
This usually doesn't work, as IPv6 rate limiting is usually done per /64 range (which is the smallest subnet allowed per the IPv6 spec), not per individual IP.
-
Most service providers like Vultr provide /64 ip ranges, which provide us with 18,446,744,073,709,551,616 addresses. In theory, we could use IPv6 and rotate the IP address we use for every request, bypassing this ratelimit.
This usually doesn't work, as IPv6 rate limiting is usually done per /64 range (which is the smallest subnet allowed per the IPv6 spec), not per individual IP.
Ipv6 catching strays
-
Our names, numbers, and home addresses used to be in a book delivered to everyone's door or found stacked in a phone booth on the street. That was normal for generations.
It's funny how much fuckwits can change the course of society and how we can't have nice things.
-
Eventually, I had a PoC running, but I was still getting the captcha? It seemed that for whatever reason, datacenter IP addresses using the JS disabled form were always presented with a captcha, damn!
The simplest answer is probably the right one. They are used for bots.
-
I set up my GranCentral, now Google Voice, account using a VoIP number from a company that went defunct many years ago. My Google accounts use said Google Voice phone number to validate because GrandCentral wasn't owned by Google back then. I assume this use case is so small, there is no point fixing it. So essentially, my accounts fall into a loop where google leads to google, etc.
heh
-
God, I hate security "researchers". If I posted an article about how to poison everyone in my neighborhood, I'd be getting a knock on the door. This kind of shit doesn't help anyone. "Oh but the state-funded attackers, remember stuxnet". Fuck off.
-
Google, Apple, and rest of big tech are pregnable despite their access to vast amounts of capital, and labor resources.
I used to be a big supporter of using their "social sign on" (or more generally speaking, single sign on) as a federated authentication mechanism. They have access to brilliant engineers thus naively thought - "well these companies are well funded, and security focused. What could go wrong having them handle a critical entry point for services?”
Well as this position continues to age poorly, many fucking aspects can go wrong!
- These authentication services owned by big tech are much more attractive to attack. Finding that one vulnerability in their massive attack vector is difficult but not impossible.
- If you use big tech to authenticate to services, you are now subject to the vague terms of service of big tech. Oh you forgot to pay Google store bill because card on file expired? Now your Google account is locked out and now lose access to hundreds of services that have no direct relation to Google/Apple
- Using third party auth mechanisms like Google often complicate the relationship between service provider and consumer. Support costs increase because when a 80 yr old forgot password or 2FA method to Google account. They will go to the service provider instead of Google to fix it. Then you spend inordinate amounts of time/resources trying to fix issue. These costs eventually passed on to customer in some form or another
Which is why my new position is for federated authentication protocols. Similar to how Lemmy and the fediverse work but for authentication and authorization.
Having your own IdP won’t fix the 3rd issue, but at least it will alleviate 1st and 2nd concerns
-
Our names, numbers, and home addresses used to be in a book delivered to everyone's door or found stacked in a phone booth on the street. That was normal for generations.
It's funny how much fuckwits can change the course of society and how we can't have nice things.
Right, but when everyone got phone books, those were only shared locally in the town. It would be pretty hard to figure out someones phone number from across the state/country without the internet unless you knew someone in the town.
You could also pay to be unlisted, which is a luxury long since gone. How cool would it be to make your data 'unlisted' by paying a small monthly fee.
-
Our names, numbers, and home addresses used to be in a book delivered to everyone's door or found stacked in a phone booth on the street. That was normal for generations.
It's funny how much fuckwits can change the course of society and how we can't have nice things.
Still are. I got a phone book delivered a week ago, I shit thee not. Granted I'm on a small island and the book is small too. But like, you can pay to have your number removed from the book. Can you have it removed from this? Not to mention all the 2FA stuff that can be connected to the phone number. Someone clones your number or takes it and suddenly they've got access to a whole lot of your login stuff.
-
Right, but when everyone got phone books, those were only shared locally in the town. It would be pretty hard to figure out someones phone number from across the state/country without the internet unless you knew someone in the town.
You could also pay to be unlisted, which is a luxury long since gone. How cool would it be to make your data 'unlisted' by paying a small monthly fee.
Nevermind
-
Right, but when everyone got phone books, those were only shared locally in the town. It would be pretty hard to figure out someones phone number from across the state/country without the internet unless you knew someone in the town.
You could also pay to be unlisted, which is a luxury long since gone. How cool would it be to make your data 'unlisted' by paying a small monthly fee.
It would be even cooler if we had a right to privacy
-
God, I hate security "researchers". If I posted an article about how to poison everyone in my neighborhood, I'd be getting a knock on the door. This kind of shit doesn't help anyone. "Oh but the state-funded attackers, remember stuxnet". Fuck off.
I think the method of researching and then informing the affected companies confidentially is a good way to do it but companies often ignore these findings. It has to be publicized somehow to pressure them into fixing the problem.
-
Still are. I got a phone book delivered a week ago, I shit thee not. Granted I'm on a small island and the book is small too. But like, you can pay to have your number removed from the book. Can you have it removed from this? Not to mention all the 2FA stuff that can be connected to the phone number. Someone clones your number or takes it and suddenly they've got access to a whole lot of your login stuff.
My phone book is smaller than a novel and only has yellow pages these days.
-
God, I hate security "researchers". If I posted an article about how to poison everyone in my neighborhood, I'd be getting a knock on the door. This kind of shit doesn't help anyone. "Oh but the state-funded attackers, remember stuxnet". Fuck off.
Without researchers like that, someone else would figure it out and use it maliciously without telling anyone. This researcher got Google to close the loophole that the exploit requires before publicly disclosing it.
-
Casually rotating 18,446,744,073,709,551,616 IP addresses to bypass rate limits.
I am not in IT security, but find it fascinating what clever tricks people use to break (into) stuff.
In a better world, we might use this energy for advancing humanity instead of looking how we can hurt each other. (Not saying the author is doing that, just lamenting that ITS is necessary due to hostile actors in this world. )
-
God, I hate security "researchers". If I posted an article about how to poison everyone in my neighborhood, I'd be getting a knock on the door. This kind of shit doesn't help anyone. "Oh but the state-funded attackers, remember stuxnet". Fuck off.
I think it's important for users to know how vulnerable they really are and for providers to have a fire lit under their ass to patch holes. I think it's standard practice to alert providers to these finds early, but I'm guessing a lot of them already knew about the vulnerabilities and often don't give a shit.
Compared to airing this dirty laundry I think the alternatives are potentially worse.
-
Still are. I got a phone book delivered a week ago, I shit thee not. Granted I'm on a small island and the book is small too. But like, you can pay to have your number removed from the book. Can you have it removed from this? Not to mention all the 2FA stuff that can be connected to the phone number. Someone clones your number or takes it and suddenly they've got access to a whole lot of your login stuff.
Pay to have it removed! That sounds like blackmail doxing.
-
It would be even cooler if we had a right to privacy
No doubt, lucky us, we get neither...
-
Bitchat is a new private Bluetooth messaging app that doesn’t need the internet – here’s how it works
Technology 1
1
-
-
Beeper's all-in-one messaging app relaunches with an on-device model and premium 10$/mo and 50$/mo upgrades
Technology 1
1
-
Mastodon: New Terms of Service IP clause cannot be terminated or revoked, not even by deleting content
Technology 1
1
-
-
-
-