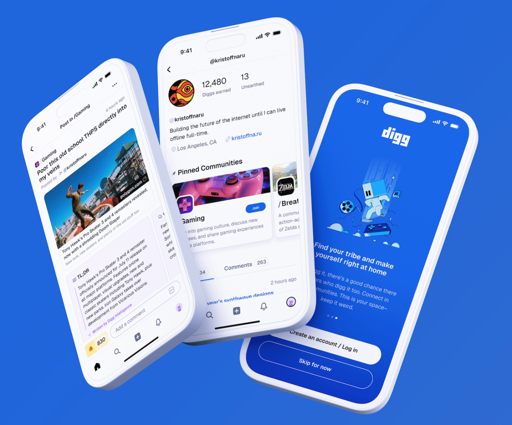
Here's your first look at the rebooted Digg | TechCrunch
-
What's wrong with AI summaries? AI has it's uses. A long as it's just adding some metadata I don't see nothing wrong with it.
For me the big questions is what are they going to do to stop bots, spam and internet points farming. So far they didn't reveal any plans.
What's wrong with AI summaries?
It never stops there though, they never just write their summary and leave it alone they always have to have the AI do more and more until it eventually takes over the entire platform.
-
Oh look, another centralized social media platform that will eventually get enshittified
This one is different, it starts enshittified and enshittifies further
-
concepts that have been whipped up in Photoshop aren't "first looks"
The article says an iOS app was released to testers.
-
The article says an iOS app was released to testers.
but that's not my first look as the title states.
-
What's wrong with AI summaries? AI has it's uses. A long as it's just adding some metadata I don't see nothing wrong with it.
For me the big questions is what are they going to do to stop bots, spam and internet points farming. So far they didn't reveal any plans.
The thing that's mostly wrong with AI summaries is that people don't click through to the page the summary summarizes. So those sites don't get ad revenue. That's ad revenue is the backbone of the internet for a lot of sites. If there's no site posting the information then the AI has nothing to summarize and provide an overview of. The pivot to AI LLM's is likely to kill the companies who aggregate links, and they're pushing for it hoping to make it profitable in the long term because they've been actively enshittifying ad aggregation via search for the purposes of big number must go up (you know, for the shareholders). It's defeatist to the current business model of most of the internet. And the shareholders do not care so long as they get their money.
-
its not a comment its in the post and its alpha, they'll prob add an option for it to be closed by default.
deleted by creator
-
The thing that's mostly wrong with AI summaries is that people don't click through to the page the summary summarizes. So those sites don't get ad revenue. That's ad revenue is the backbone of the internet for a lot of sites. If there's no site posting the information then the AI has nothing to summarize and provide an overview of. The pivot to AI LLM's is likely to kill the companies who aggregate links, and they're pushing for it hoping to make it profitable in the long term because they've been actively enshittifying ad aggregation via search for the purposes of big number must go up (you know, for the shareholders). It's defeatist to the current business model of most of the internet. And the shareholders do not care so long as they get their money.
The thing that's mostly wrong with AI summaries is that people don't click through to the page the summary summarizes. So those sites don't get ad revenue.
Don’t ad blockers have a similar effect?
-
The thing that's mostly wrong with AI summaries is that people don't click through to the page the summary summarizes. So those sites don't get ad revenue. That's ad revenue is the backbone of the internet for a lot of sites. If there's no site posting the information then the AI has nothing to summarize and provide an overview of. The pivot to AI LLM's is likely to kill the companies who aggregate links, and they're pushing for it hoping to make it profitable in the long term because they've been actively enshittifying ad aggregation via search for the purposes of big number must go up (you know, for the shareholders). It's defeatist to the current business model of most of the internet. And the shareholders do not care so long as they get their money.
There are summaries of articles on lemmy, just not generated by LMMs. What's the difference?
-
This post did not contain any content.
Why the fuck would I want my link aggregator to have a leaderboard?
People competing for fake internet points is already driving some of the worst patterns we're seeing on the social web. Imagine putting that shit front and center.
-
The thing that's mostly wrong with AI summaries is that people don't click through to the page the summary summarizes. So those sites don't get ad revenue.
Don’t ad blockers have a similar effect?
Not exactly. People don't click on ads when ads are blocked. But ad aggregation companies get paid in a couple of different ways. Click through is a big one, but ad impressions (eyeballs that supposedly viewed an ad) are also a thing. And impressions pay, just not as well as clickthroughs. Ad companies haven't stopped paying aggregates for ad space. That's why ads on paid services have gotten more egregious. It's not because they aren't getting paid. It's because they want both.
For what it's worth, you can (and some do) pay for subscriptions to websites or services on the internet. But nobody is paying ad aggregation companies with the intent of seeing ads regardless of the reality.
Also, ad blocking as a whole is for security as much as it is for quality of life. Ad aggregation companies have a habit of taking the money and asking questions only when they get complaints (if then) and as a result, they don't leave users who want to protect themselves another choice.
Of course, there's also the fact that one way or another the web can't just be free. Someone somewhere has to pay for the resources that make it run and the upkeep it requires.
-
There are summaries of articles on lemmy, just not generated by LMMs. What's the difference?
Depends. I often click on articles based on the summary because the article link is usually posted before the summary is. Sometimes the summary doesn't really explain enough for me to understand. Other times I want to know more. But when you use chatgpt to answer a query usually you don't leave that page in order to get more information and that's the problem I'm pointing out. Usually you don't even have a link to where the information in the summary came from either (my experience is limited to Google's Gemini, which I don't use, but which for a while was front and center on any query I typed in).
-
deleted by creator
Becuase the app is in alpha lol, its janky everywhere, has no settings or customizability uet, cant even make communities yet, ill give them the benefit of the doubt that you can turn them off or auto hide them
-
Becuase the app is in alpha lol, its janky everywhere, has no settings or customizability uet, cant even make communities yet, ill give them the benefit of the doubt that you can turn them off or auto hide them
So not only was the AI put front and center, it was also put in first?!
I've looked at plenty of alpha software before, and I've seen plenty of incomplete features. I understand that one has to give an unfinished product leeway. But devs do not simply accidentally add a whole feature into an app. Or if this was somehow all a huge coincidental mistake, they made a massive PR blunder.
-
this would-be Reddit competitor, built for the AI era
Oh no...
The founders think that the internet is being flooded with bots and AI agents, which will create demand for online communities like Digg that foster real human connections.
Okay, Digg has my cautious attention...
Beneath posts, Digg is leveraging AI to summarize the article’s content.
And they lost me.
All valid points, and he base truth around all this is there's no way this is the original Digg anyway. Someone bought the name rights and have Diggs' corpse strung up with a painted on smile.
-
Why the fuck would I want my link aggregator to have a leaderboard?
People competing for fake internet points is already driving some of the worst patterns we're seeing on the social web. Imagine putting that shit front and center.
Well you see there's gonna be a digg store where all your diggs can get you a virtual hat for your diggdug Ai virtual toon man guy.
-
Why the fuck would I want my link aggregator to have a leaderboard?
People competing for fake internet points is already driving some of the worst patterns we're seeing on the social web. Imagine putting that shit front and center.
Because those shitty patterns make the platform valuable. It's about creating investor value, end user be damned.
-
So not only was the AI put front and center, it was also put in first?!
I've looked at plenty of alpha software before, and I've seen plenty of incomplete features. I understand that one has to give an unfinished product leeway. But devs do not simply accidentally add a whole feature into an app. Or if this was somehow all a huge coincidental mistake, they made a massive PR blunder.
Guess this particilar use of ai just isnt an issue for me, I personally have more problems with lemmys use of generative ai and hyping it up
-
So not only was the AI put front and center, it was also put in first?!
I've looked at plenty of alpha software before, and I've seen plenty of incomplete features. I understand that one has to give an unfinished product leeway. But devs do not simply accidentally add a whole feature into an app. Or if this was somehow all a huge coincidental mistake, they made a massive PR blunder.
summaries are a non issue, stealing other ppls work to pass of on your own is
-
nods enthusiastically in Mbin
How's mbin doing, lately? I switched (back) to Lemmy when kbin shuttered and haven't kept up with it.
-
The hero no one wanted, or needed
But other than that. Cool
Cool how?