UK households could face VPN 'ban' after use skyrockets following Online Safety Bill
-
Honest question but what makes you think that would happen? Do most businesses use VPNs?
I work for a government agency and VPNs are vital for day to day operations.
-
Prominent backbench MP Sarah Champion launched a campaign against VPNs previously, saying: “My new clause 54 would require the Secretary of State to publish, within six months of the Bill’s passage, a report on the effect of VPN use on Ofcom’s ability to enforce the requirements under clause 112.
"If VPNs cause significant issues, the Government must identify those issues and find solutions, rather than avoiding difficult problems.” And the Labour Party said there were “gaps” in the bill that needed to be amended.
You cant ban vpns, its easy for tech people to set up a vpn server on any server on the internet and connect to it. Wireguard for example, super simple.
-
Most conventional VPNs, e.g. OpenVPN, WireGuard, AnyConnect, PPTP/L2TP, IKEv2/IPsec, etc., actually don't work in China. Technology-wise GFW is quite sophisticated and conventional VPNs are not designed for censorship circumvention anyway.
You'll have to use things like Shadowsocks or V2Ray, which is out of the reach of most people.
Edit: You meant they dont work to access things outside of China of course.
-
Prominent backbench MP Sarah Champion launched a campaign against VPNs previously, saying: “My new clause 54 would require the Secretary of State to publish, within six months of the Bill’s passage, a report on the effect of VPN use on Ofcom’s ability to enforce the requirements under clause 112.
"If VPNs cause significant issues, the Government must identify those issues and find solutions, rather than avoiding difficult problems.” And the Labour Party said there were “gaps” in the bill that needed to be amended.
labour really doesn't want people to access lgbtq safe spaces and resources huh?
-
Prominent backbench MP Sarah Champion launched a campaign against VPNs previously, saying: “My new clause 54 would require the Secretary of State to publish, within six months of the Bill’s passage, a report on the effect of VPN use on Ofcom’s ability to enforce the requirements under clause 112.
"If VPNs cause significant issues, the Government must identify those issues and find solutions, rather than avoiding difficult problems.” And the Labour Party said there were “gaps” in the bill that needed to be amended.
I was very concerned like 15+ years ago when all the CCTV cameras went up. In some ways better than the US and in other ways worse. In the US corporations get free reign all over your data while in Europe, corporations more restricted but government gets a deep claw into people's digital lives. I think if the American mega tech companies were based in Europe, Europe would be corporations have free reign over your data. Just a matter of jurisdiction. The power and influence politicians and rich people can do domestically
-
Most conventional VPNs, e.g. OpenVPN, WireGuard, AnyConnect, PPTP/L2TP, IKEv2/IPsec, etc., actually don't work in China. Technology-wise GFW is quite sophisticated and conventional VPNs are not designed for censorship circumvention anyway.
You'll have to use things like Shadowsocks or V2Ray, which is out of the reach of most people.
The Great Firewall doesn't block by protocol. If you set up your own OpenVPN server, you can still connect to it. I've done this many times in my trips to China, and it's worked fine. That being said, they still do seem to throttle connections to international servers, though this happens to all servers, even those that are not blocked. There are many clandestine VPN operators in China who spin up their own VPN servers and sell the service. They are mostly OpenVPN-based.
My university used Cisco AnyConnect, and I was able to successfully connect to the university VPN servers as well.
The limited experimentation I have conducted seems to indicate that the Great Firewall blocks by IP and not by protocol.
-
How is this even feasible? People need them for work, business, school etc. The UK is going nuts with the attempts to regulate the internet.
Take China for example. There is a common misconception that all VPNs are illegal in China. That's not fully true. In China, VPNs are legal and must obtain a licence from the Ministry of Public Security, like all other online businesses. This also means that they have to agree to monitoring and censorship from the Government, so you can't use legal VPN services to bypass the firewall in China.
-
Prominent backbench MP Sarah Champion launched a campaign against VPNs previously, saying: “My new clause 54 would require the Secretary of State to publish, within six months of the Bill’s passage, a report on the effect of VPN use on Ofcom’s ability to enforce the requirements under clause 112.
"If VPNs cause significant issues, the Government must identify those issues and find solutions, rather than avoiding difficult problems.” And the Labour Party said there were “gaps” in the bill that needed to be amended.
What if we all started using I2P for most stuff? The governments couldn't do anything about it.
-
You cant ban vpns, its easy for tech people to set up a vpn server on any server on the internet and connect to it. Wireguard for example, super simple.
yup just did it this morning on my server because now I'm moving my stuff, yet again, away from European companies because of all this. it was painfully simple and easy. I just followed a guide I found on a linux blog and within 10minutes I had a VPN of my own up and running.
-
You cant ban vpns, its easy for tech people to set up a vpn server on any server on the internet and connect to it. Wireguard for example, super simple.
Oh, sweet summer child. Of course you can ban them. Lawmakers don't always care about the technicality of things, because in most cases they don't have to.
You can't prevent VPN from existing, and short of a very tightly curated whitelist of services, you can't prevent people from actually using them, sure. Unless you're on the side of the state, the Law, and the enforcement. In which case, you can. A blanket ban on VPN usage is the perfect gateway to "we've seen traffic from your house toward a known VPN server, so, blam, arrest". And it does not have to stop at known server.
Given the regular tries to outright ban encryption, this is the perfect venue to mass target encrypted communications. Depending on the wording, the mere presence of unobservable traffic could be enough for an arrest.
If what I'm saying here sound dystopian to you, just remember that not only most of this was actually tried (and aborted) time after time, but also that until quite recently, the general public actually using strong encryption was illegal in many places, including our western countries, and experiments to make state spyware mandatory are also a recurrent thing (which might take hold with the "ID verification through your phone" apps soon).
-
Prominent backbench MP Sarah Champion launched a campaign against VPNs previously, saying: “My new clause 54 would require the Secretary of State to publish, within six months of the Bill’s passage, a report on the effect of VPN use on Ofcom’s ability to enforce the requirements under clause 112.
"If VPNs cause significant issues, the Government must identify those issues and find solutions, rather than avoiding difficult problems.” And the Labour Party said there were “gaps” in the bill that needed to be amended.
for those in the UK and/or Other places in Europe just know it's so painfully easy to either set up your own VPN or just use something like Mullvad.
I set up my own VPN this morning for the first time on my server and it took less than 10minutes. plenty of guides online on how to do it.
-
Lol what is going on over there. The UK is becoming more dystopian by the day.
They looked at their calendar and thought "Oh shit!" when they saw they were overdue to start V for Vendetta.
-
Oh, sweet summer child. Of course you can ban them. Lawmakers don't always care about the technicality of things, because in most cases they don't have to.
You can't prevent VPN from existing, and short of a very tightly curated whitelist of services, you can't prevent people from actually using them, sure. Unless you're on the side of the state, the Law, and the enforcement. In which case, you can. A blanket ban on VPN usage is the perfect gateway to "we've seen traffic from your house toward a known VPN server, so, blam, arrest". And it does not have to stop at known server.
Given the regular tries to outright ban encryption, this is the perfect venue to mass target encrypted communications. Depending on the wording, the mere presence of unobservable traffic could be enough for an arrest.
If what I'm saying here sound dystopian to you, just remember that not only most of this was actually tried (and aborted) time after time, but also that until quite recently, the general public actually using strong encryption was illegal in many places, including our western countries, and experiments to make state spyware mandatory are also a recurrent thing (which might take hold with the "ID verification through your phone" apps soon).
Thanks for this. I think it's really important to point out that merely having unobservable traffic could be a trigger for this.
We can't avoid taking these threats seriously because we think we are smarter.
-
I don't think it's even possible to get rid of VPNs without outright banning encryption. If I set up a VPN that uses an obscure port and the traffic is encrypted, how are they going to know it's even a VPN?
Attached below is a Wireshark trace I obtained by sniffing my own network traffic.

I want to draw your attention to this part in particular:
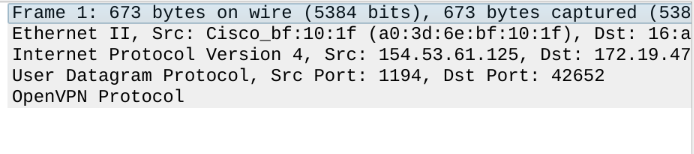
Underneath "User Datagram Protocol", you can see the words "OpenVPN Protocol". So anyone who sniffs my traffic on the wire can see exactly the same thing that I can. While they can't read the contents of the payload, they can tell that it's OpenVPN traffic because the headers are not encrypted. So if a router wanted to block OpenVPN traffic, all they would have to do is drop this packet. It's a similar story for Wireguard packets. An attacker can read the unencrypted headers and learn
- The size of the transmission
- The source and destination IP addresses by reading the IP header
- The source and destination ports numbers by reading the TCP or UDP headers
- The underlying layers, up until the point it hits an encrypted protocol (such as OpenVPN, TLS, or SSH)
-
I doubt their corpo overlords would allow a VPN ban considering the amount of companies that use them.
It would be trivial for them to write it so it bans it for citizen use but is allowed for corporate and government use. The people have no rights anymore
-
Thanks for this. I think it's really important to point out that merely having unobservable traffic could be a trigger for this.
We can't avoid taking these threats seriously because we think we are smarter.
We arent smarter. Actually most people here have no voice or influence outside of their computer screen.
We can use some tech, sure. But I very much challenge the idea that we are smarter as a group than other university students.
But since a lot of us have poor social skills, we compensate by thinking we are smarter or better, when we should instead train our social skills and stop thinking like that.
-
They couldn't switch off VPNs for businesses. I work in a hospital and we use VPNs to create secure tunnels to other third party health care companies as well as NHS adjacent health services amongst other things. This is to protect patient sensitive data amongst other things. This would cripple our service and go against NHS england and government requirements for the secure transfer and sharing of data.
This would have to be public VPNs only. Despite the fact that it would be complete bullshit either way.
Well, you could just go back to sending stuff by fax machine forever, but then instead of even using the fax machine to sync patient data just make the patients fill out their own entire medical history from scratch every time they go to a different doctor and take their word for it.
-
We arent smarter. Actually most people here have no voice or influence outside of their computer screen.
We can use some tech, sure. But I very much challenge the idea that we are smarter as a group than other university students.
But since a lot of us have poor social skills, we compensate by thinking we are smarter or better, when we should instead train our social skills and stop thinking like that.
I agree, but I think it is a trap we can easily fall into. Especially in this case.
-
I agree, but I think it is a trap we can easily fall into. Especially in this case.
Yeah I agree. We have to wake up a bit. Real change happens outside of this place.
-
Prominent backbench MP Sarah Champion launched a campaign against VPNs previously, saying: “My new clause 54 would require the Secretary of State to publish, within six months of the Bill’s passage, a report on the effect of VPN use on Ofcom’s ability to enforce the requirements under clause 112.
"If VPNs cause significant issues, the Government must identify those issues and find solutions, rather than avoiding difficult problems.” And the Labour Party said there were “gaps” in the bill that needed to be amended.
To me it looks like every government in the world is pro-surveillance and anti-privacy; they're just all at different stages of depth into those ideologies done in practice. Privacy and anti-surveillance against foreign governments and corporations, pro for domestic. And I continue decade after decade to say that you should fear your domestic government far more than any foreign unless you're a country that may have US and allies bombing/droning and paratrooping your country. Countries with a modern enough military mostly have to worry about their own government rather than foreign governments




