Matrix.org is Introducing Premium Accounts
-
This post did not contain any content.
The Matrix.org Foundation is a non-profit and only relies on donations to operate. Its core mission is to maintain the Matrix Specification, but it does much more than that.
Non-profit… only relies on donations…
This was taken quite literally at the bottom of that article.
-
We have been communicating on the lack of funds in the Foundation for a while now, the latest being here. And whilst we’ve been working hard to gather new members and are happy to see the number of logos increasing (thank you all for seeing the need for Matrix to stay independent and safe, and the value in supporting it!), none of the big players in the ecosystem have actually committed to one of the higher membership tiers, so we need to find other ways towards sustainability.

Sounds like that business plan isn't working out like you hoped...
And/Or not enough users care to use your product.

 ️
️The plan was to rely on donations, which doesn't usually work for hosted products.
-
For just $19.95 a month you can talk to all your friends!
You can do that for free. But for that low, low price, you can talk to your friends with a Matrix Green checkmark next your name! #worthit
-
The Matrix.org Foundation is a non-profit and only relies on donations to operate. Its core mission is to maintain the Matrix Specification, but it does much more than that.
Non-profit… only relies on donations…
This was taken quite literally at the bottom of that article.
The context in the article is important. Similar to what FUTO preaches-- people don't donate. That's why corporate solutions usually win. Better to charge a bit of money so we can have nice things.
-
You can do that for free. But for that low, low price, you can talk to your friends with a Matrix Green checkmark next your name! #worthit
A green check!!!! Wow! Sign me up baby!
-
Not trying to be a dick but the Executive Director can take a fucking pay cut.
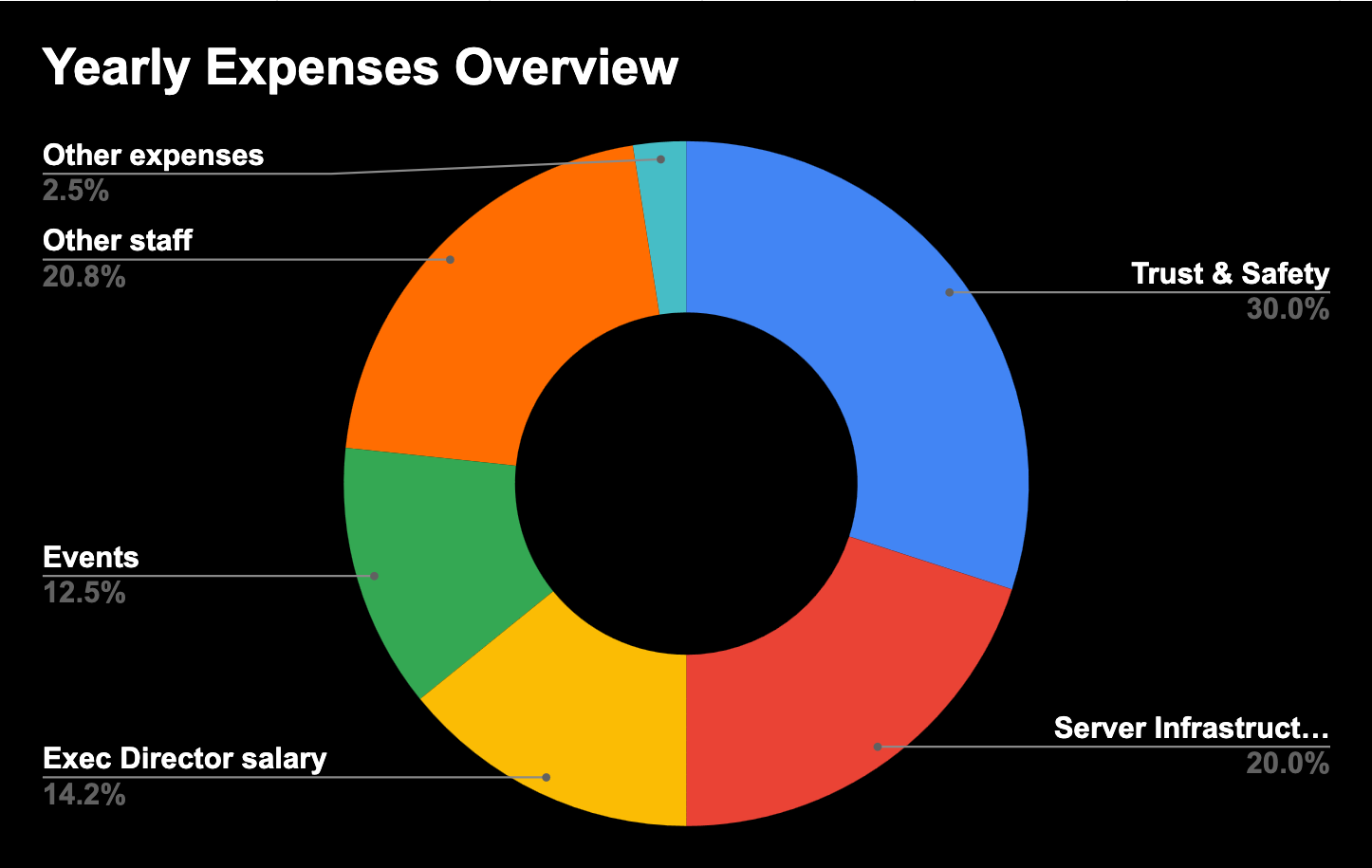
I found a reddit thread from 4 months ago where he said his salary was $170k/year. I'm not saying he is making obscene money, but if that's nearly 15% of all operating costs he can shave that down to $80k-$100k and still live comfortably if he's willing to accept a more austere standard of living.
I'm not saying he doesn't deserve to be paid well, but he's getting a damn sight better pay than moderators and community managers who seem to make up 50% of the budget for multiple people: the trust and safety team as well as the other employees at the foundation.
170k for running a company? Shit. I wouldn't do that. You can make just as much being a halfway competent developer, and it's way less stress.
-
Now 9 wonder if there's a similar report for Mozilla
You can pull the form 990 for any non-profit in the US pretty easily. Here's Mozilla's: https://projects.propublica.org/nonprofits/organizations/200097189
-
My understanding is that Matrix is a nonprofit.
Non-profit organizations still exist within the capitalist system. Just because they don't pay out dividends to shareholders doesn't mean they can't be exploitative. If a non-profit makes a lot of money, the people who run it just increase their own salaries. Happens all the time. And yes, non-profits exploit labor all the time. Local arts councils are an easy example of this. Run an art show where the venue and food are donated. They take a fee at the door, ask for donations throughout, and require a cut of any art sold. If there's a bar, they get a cut of that too. The artists who enabled the show to even exist did all their labor for free in exchange for exposure and maybe selling something. They see none of the take though. Sounds pretty capitalist to me.
-
The context in the article is important. Similar to what FUTO preaches-- people don't donate. That's why corporate solutions usually win. Better to charge a bit of money so we can have nice things.
The same people that enshitified open source licences ?
-
Non-profit organizations still exist within the capitalist system. Just because they don't pay out dividends to shareholders doesn't mean they can't be exploitative. If a non-profit makes a lot of money, the people who run it just increase their own salaries. Happens all the time. And yes, non-profits exploit labor all the time. Local arts councils are an easy example of this. Run an art show where the venue and food are donated. They take a fee at the door, ask for donations throughout, and require a cut of any art sold. If there's a bar, they get a cut of that too. The artists who enabled the show to even exist did all their labor for free in exchange for exposure and maybe selling something. They see none of the take though. Sounds pretty capitalist to me.
I never said it wasn't capitalist, just that being bad nonprofit should afford a little more leniency when it comes to "free labor." Matrix is FOSS, the Matrix foundation exists to drive its development, and its whole point is to provide a replacement for exploitative products. Such an organization soliciting donations makes a ton of sense, and donations can take the form of code, money, or even free labor (moderation).
So yeah, I'm absolutely willing to give them a pass on asking for such donations, and I think they should replace some of the money they're spending on moderation w/ more development time.
-
If they have to pay their Executive Director that much as a non-profit and are failing to meet their funding goals as a non-profit the amount he gets paid has fuck-all to do with where he lives, and has everything to do with him failing at his job to secure funding.
So we're supposed to fund this guys lifestyle as people who donate to the project while the project itself twists in the wind? Give me a fucking break, dude. This is how you set your organization up for failure.
It's not like a bunch of his work couldn't be done remotely. Maybe he should move to bumfuck Idaho so he can afford to run this god damned foundation. But nooooo, he needs to live in some obscenely expensive area, right? Bull. Shit.
him failing at his job to secure funding
Is this thread not about a new attempt to secure funding?
-
The Matrix.org Foundation is a non-profit and only relies on donations to operate. Its core mission is to maintain the Matrix Specification, but it does much more than that.
Non-profit… only relies on donations…
This was taken quite literally at the bottom of that article.
At some point donations become unsustainable. Like literally their options are to start charging or close up shop.
The smarter thing to do would be to rotate instances on sign-up to decentralize the Matrix-verse but it's probably too late now.
-
Not trying to be a dick but the Executive Director can take a fucking pay cut.

I found a reddit thread from 4 months ago where he said his salary was $170k/year. I'm not saying he is making obscene money, but if that's nearly 15% of all operating costs he can shave that down to $80k-$100k and still live comfortably if he's willing to accept a more austere standard of living.
I'm not saying he doesn't deserve to be paid well, but he's getting a damn sight better pay than moderators and community managers who seem to make up 50% of the budget for multiple people: the trust and safety team as well as the other employees at the foundation.
I’m not saying he is making obscene money
Then I am: he is making obscene money. Converted that's like 125k GBP, you can buy a house for cash every 3 years in the UK from that much money O.o (Ok, every 6 years if you spend half of it one living costs.) It's almost 7 times the minimum wage here.
-
The same people that enshitified open source licences ?
People deserve to get paid on their work, and currently the best way to do that and survive in America is to work on completely closest source products that don't respect their users. Open source is probably the most respectful but doesn't work well as a business. We need something that works reliably for delivering real products that will achieve mass adoption. I think these source available licenses are that.
-
People deserve to get paid on their work, and currently the best way to do that and survive in America is to work on completely closest source products that don't respect their users. Open source is probably the most respectful but doesn't work well as a business. We need something that works reliably for delivering real products that will achieve mass adoption. I think these source available licenses are that.
You know what else source-available licences do ?
Put restrictions like you cannot make money from the forks. Forks are the lifeblood of FOSS.
-
I’m not saying he is making obscene money
Then I am: he is making obscene money. Converted that's like 125k GBP, you can buy a house for cash every 3 years in the UK from that much money O.o (Ok, every 6 years if you spend half of it one living costs.) It's almost 7 times the minimum wage here.
I make only slightly less than that in American dollars and I’m not at all close to running a company. I’m very solidly lower middle class I will also not be buying a hour for another 5-6 years.
That is a very modest amount of money for his role.
-
This post did not contain any content.
Matrix org isn't obligated to run a public instance at all - they could stick to developing the spec, and let other people run instances.
And honestly maybe they should, because then we wouldn't have this huge consolidation problem on matrix.org in the first place.
-
Wish the homeserver portability would be worked on more. The ability to change homeserver would really allow people to more easily move on from matrix.org.
Myself included ;).
Optimally it would even allow the switch "after the fact", so after your original homeserver is down, assuming your client has a local copy of the server-side secret storage. It would need to be based on some cryptographic identity then, I suppose.
Yes, this would be a great feature - but it's a big issue to implement. It's talked about in this video, worth watching if you're curious about it.
As far as status go, this issue on the matrix spec is what you want to follow.
-
xmpp is still the best, nobody's ever going to change my mind. jabber 4 lyfe!
From federated protocols yes! But I would like to see something really p2p to take over. So far no luck
-
This post did not contain any content.
Premium, dude!
Jokes aside, fuck this shit.







