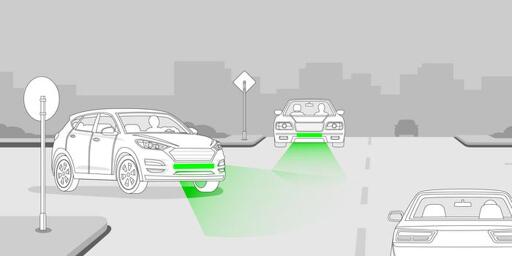
Front Brake Lights Could Drastically Diminish Road Accident Rates
-
BMW has implemented this in the US market for the past 20 years or so at least. Under heavy braking, additional brake lights turn on. I believe they call that Brake Force Display. I’m sure they’re not the only manufacturer to do this, too
Plenty of cars flash their brake lights when ABS(/ESP?) engages, which is reasonable and should be a legal requirement IMO.
There's lots of room to give additional info in between that and "brake light is on because the driver doesn't understand that they can do mild adjustments by letting off the gas / stupid bitch-ass VW PHEV computer thinks using cruise control downhill with electric regen requires the motherfucking brake lights". It's like no-one realizes or cares that brake lights lose all purpose if they're on when the car isn't meaningfully decelerating. ARGH.
-
and honestly i have the same problem with that intended use. it often looks like a stopped car is attempting to turn out into traffic. IMO emergency lights should have a faster blink pattern or something to differentiate from turn signals.
There's a programmable flasher relay that does exactly this. It's specific to certain Toyota/Lexus and Subarus from the 2000s to mid-2010s, but it's something. I have one in my 2008 Sienna - the "emergency flasher" part is programmed to strobe, kinda like a tow truck. I like it.
-
Japan introduced brake lights that increase intensity based on how hard the driver was braking. 20+ years ago. They tested it in the US and drivers found it to be “confusing.”
probably because thats a terrible way to do it. It would be noticeable if a car started braking and then started braking much harder, but if they slam on the brakes you don't see anything change, just a normal brake light.
-
I still think rear signaling could be improved dramatically by using a wide third-brake light to show the intensity of braking.
For example -- I have seen some aftermarket turn signals which are bars the width of the vehicle, and show a "moving" signal starting in the center and then progressing towards the outer edge of the vehicle.
So now take that idea for brake. When you barely have your foot on the brake pedal, it would light a couple lights in the center of your brake signal. Press a little harder and now it's lighting up 1/4 of the lights from the center towards the outside edge of the vehicle. And when you're pressing the brake pedal to the floor, all of the lights are lit up from the center to the outside edges of the vehicle. The harder you press on the pedal, the more lights are illuminated.
Now you have an immediate indication of just how hard the person in front of you is braking. With the normal on/off brake signals, you don't know what's happening until moments later as you determine how fast you are approaching that car. They could be casually slowing, or they could be locking up their wheels for an accident in front of them.
Seems much more complicated than having the brake lights rapidly flash during hard braking. But of course we couldn't do that in the US because our turn signals/hazard lights are red
-
I don't know where you are but rear fogs aren't illegal in the rain here and from experience they are nothing but helpful in heavy rain and white out snow. I am always so so sooo glad when someone in front of me is using them when it's absolutely pouring. You really have to not be paying attention not to notice that it's two lights and not three and somehow mistake them for stop lights.
In fact, Transport Canada recommends using them in fog, rain, or snow.
Use only if driving in fog, rain or snow as these lights can be confused with stop lights, distracting other drivers.
Using your vehicle lights to see and be seen
About the new vehicle lighting standard for cars in 2021 and tips on how to use your lights safely now.
Transport Canada (tc.canada.ca)
II. - Le ou les feux arrière de brouillard ne peuvent être utilisés qu'en cas de brouillard ou de chute de neige. ☞ https://www.legifrance.gouv.fr/codes/article_lc/LEGIARTI000006842263
Feux de brouillard arrière : ils sont indiqués uniquement en cas de brouillard ou de chute de neige (mais jamais sous la pluie en raison de leur trop grande intensité) ☞ https://public.codesrousseau.fr/conseils-pratiques/909-feux-de-brouillard-avant-et-arriere-quand-les-utiliser.html
-
II. - Le ou les feux arrière de brouillard ne peuvent être utilisés qu'en cas de brouillard ou de chute de neige. ☞ https://www.legifrance.gouv.fr/codes/article_lc/LEGIARTI000006842263
Feux de brouillard arrière : ils sont indiqués uniquement en cas de brouillard ou de chute de neige (mais jamais sous la pluie en raison de leur trop grande intensité) ☞ https://public.codesrousseau.fr/conseils-pratiques/909-feux-de-brouillard-avant-et-arriere-quand-les-utiliser.html
Ça c'est de l'osti de merde comme on dit ici.
-
Seems much more complicated than having the brake lights rapidly flash during hard braking. But of course we couldn't do that in the US because our turn signals/hazard lights are red
Turn signals can be either red or amber in the US.
-
Turn signals can be either red or amber in the US.
yeah, but they shouldn't be allowed to be red to begin with.
-
Not selling tanks as cars could also help. Especially with fatality rates
People don't even need car tbh. Motorbikes everywhere please. Zip zip, less traffic, everyone pays attention to road or falls and dies.
-
90% of the things that Japan introduced according to comment sections on the internet never happened (or never made it past the prototype stage) and the rest was actually introduced in Korea, not in Japan.
The Japanophilia is strong with a lot of people on the internet.
Yeah I mean I've been commuting 2 hrs a day in Japan for almost 10 years now-- you'd think I would've seen these brake lights by now
-
Since we're all throwing random ideas out here, I want to equip my vehicle with an annoyingly loud external speaker so that when someone near me does something dumb, I can personally shame them.
You are looking for war
-
If a car is braking it rides differently from one that isn't. A car is normally rather level and leans "forward" when braking.
Besides that, YOU SHOULDNT GET IN FRONT OF ANYTHING YOU ARENT SURE IS STOPPING. If it's moving fast enough that you need this, you shouldn't be trying to get in front anyways.
YOU SHOULDNT GET IN FRONT OF ANYTHING YOU ARENT SURE IS STOPPING
This, exactly. This "plan" sounds terrible to me.
No, I'm not braking to turn at the intersection you're sitting in. I'm turning into a driveway just past that intersection. If you pull in front of the green light the government says I have to have on my vehicle, I'm going to t-bone you.
-
Say you're a pedestrian and a car is coming toward you as you're entering a crosswalk. Being able to see if they are braking or not could save your life.
Ah. I see. They are emitting a green light, so I know they're braking, and it's OK to cross.
But, it turns out that they're planning on turning into a driveway past the intersection, and not into the intersection I am crossing.
That's OK. I can check "impersonate a hood ornament" off my bucket list.
We already have this problem with turn signals: there are circumstances where it would be confusing and dangerous to use them in the manner prescribed by law, and to avoid dangerous ambiguity, they should actually be used much later than the law specifies.
-
Since we're all throwing random ideas out here, I want to equip my vehicle with an annoyingly loud external speaker so that when someone near me does something dumb, I can personally shame them.
I want to equip my vehicle with an annoyingly loud external speaker so that when someone near me does something dumb, I can personally shame them.
CB radios often had a "PA" switch that sent your microphone audio to a loudspeaker under the hood.
I'd prefer a "FlameThrower" button next to the horn.
-
You are looking for war
Road rage 5000 initiate
-
People don't even need car tbh. Motorbikes everywhere please. Zip zip, less traffic, everyone pays attention to road or falls and dies.
Good luck transporting a couch on a motorbike.
-
I get what you're saying — so it's about the subconscious awareness of the state change that happens after the driver decided to go, but before the car starts moving. I can see some amount of value in that.
I still can't help but think it's going to be interpreted by many as a sign that it's safe to proceed and ignore the car rather than be prepared for any eventuality, though.
I agree that that would be a real danger, yes.
-
Good luck transporting a couch on a motorbike.
Rent a truck for cheap
-
People don't even need car tbh. Motorbikes everywhere please. Zip zip, less traffic, everyone pays attention to road or falls and dies.
That's why I bought mine!
-
I want to equip my vehicle with an annoyingly loud external speaker so that when someone near me does something dumb, I can personally shame them.
CB radios often had a "PA" switch that sent your microphone audio to a loudspeaker under the hood.
I'd prefer a "FlameThrower" button next to the horn.
Yeah this is exactly what I have in mind. I want to feel like Smokey the Bandit calling people out for bad behavior with a receiver that has a coiled cable attached to it, at a minimum.