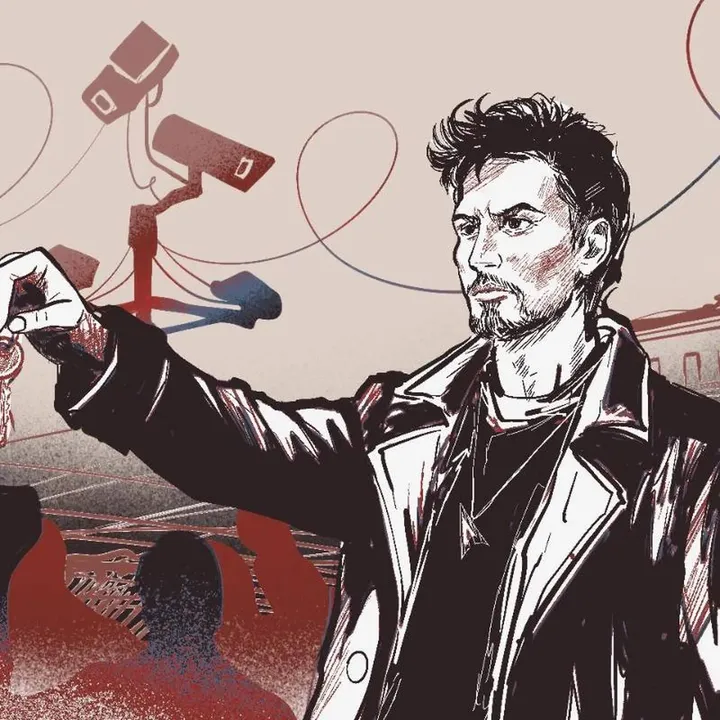
Telegram, the FSB, and the Man in the Middle: The technical infrastructure that underpins Telegram is controlled by a man whose companies have collaborated with Russian intelligence services.
-
- A company owned by a Russian network engineer named Viktor Vedeneev controls thousands of Telegram IP addresses and maintains its servers.
- Vedeneev’s other companies have a history of collaborating with Russia’s defense sector, the FSB security service, and other highly sensitive agencies.
- Because of the way Telegram’s encryption protocols work, even users who use its “end-to-end” encryption features are vulnerable to being tracked by anyone who can monitor its network traffic.
Telegram, the FSB, and the Man in the Middle
The technical infrastructure that underpins Telegram is controlled by a man whose companies have collaborated with Russian intelligence services. An investigation by IStories

(istories.media)
Not to dismiss (I agree with the premise) but is that a legit source?
-
Not to dismiss (I agree with the premise) but is that a legit source?
Yes, they are even republished by OCCRP.
-
- A company owned by a Russian network engineer named Viktor Vedeneev controls thousands of Telegram IP addresses and maintains its servers.
- Vedeneev’s other companies have a history of collaborating with Russia’s defense sector, the FSB security service, and other highly sensitive agencies.
- Because of the way Telegram’s encryption protocols work, even users who use its “end-to-end” encryption features are vulnerable to being tracked by anyone who can monitor its network traffic.

Telegram, the FSB, and the Man in the Middle
The technical infrastructure that underpins Telegram is controlled by a man whose companies have collaborated with Russian intelligence services. An investigation by IStories

(istories.media)
Look, in today's world, you get to choose who spies on you depending on your chosen platform, but spy on you they absolutely will. Wether it's the Russians, the Chinese or USA. The only way to not get spied on is to not use electronic communications at all.
-
- A company owned by a Russian network engineer named Viktor Vedeneev controls thousands of Telegram IP addresses and maintains its servers.
- Vedeneev’s other companies have a history of collaborating with Russia’s defense sector, the FSB security service, and other highly sensitive agencies.
- Because of the way Telegram’s encryption protocols work, even users who use its “end-to-end” encryption features are vulnerable to being tracked by anyone who can monitor its network traffic.

Telegram, the FSB, and the Man in the Middle
The technical infrastructure that underpins Telegram is controlled by a man whose companies have collaborated with Russian intelligence services. An investigation by IStories

(istories.media)
This is my surprised face.
-
Look, in today's world, you get to choose who spies on you depending on your chosen platform, but spy on you they absolutely will. Wether it's the Russians, the Chinese or USA. The only way to not get spied on is to not use electronic communications at all.
Look, in today's world the entire banking sector relies on private communications to operate using the Internet. Why can't private citizens get the same?
-
Look, in today's world the entire banking sector relies on private communications to operate using the Internet. Why can't private citizens get the same?
End-to-end encryption should cover you, but anything that can set up man-in-the-middle attacks is poised to defeat that.
-
End-to-end encryption should cover you, but anything that can set up man-in-the-middle attacks is poised to defeat that.
fully audited FOSS E2EE ftw
-
Look, in today's world, you get to choose who spies on you depending on your chosen platform, but spy on you they absolutely will. Wether it's the Russians, the Chinese or USA. The only way to not get spied on is to not use electronic communications at all.
Okay, who spies on me when I use e.g. Signal?
-
- A company owned by a Russian network engineer named Viktor Vedeneev controls thousands of Telegram IP addresses and maintains its servers.
- Vedeneev’s other companies have a history of collaborating with Russia’s defense sector, the FSB security service, and other highly sensitive agencies.
- Because of the way Telegram’s encryption protocols work, even users who use its “end-to-end” encryption features are vulnerable to being tracked by anyone who can monitor its network traffic.

Telegram, the FSB, and the Man in the Middle
The technical infrastructure that underpins Telegram is controlled by a man whose companies have collaborated with Russian intelligence services. An investigation by IStories

(istories.media)
He's also been arrested by western governments, and certainly there were "conditions for release".
-
Okay, who spies on me when I use e.g. Signal?
The recipient of your messages.
-
Look, in today's world, you get to choose who spies on you depending on your chosen platform, but spy on you they absolutely will. Wether it's the Russians, the Chinese or USA. The only way to not get spied on is to not use electronic communications at all.
that's not just useless defeatism, but also false. effective end to end encryption exists in multiple forms today.
signal, maybe even with a custom server.
matrix if the server is being ran on trusted hardware.
XMPP too with the right extensions.
-
-
-
Grok 4 has been so badly neutered that it's now programmed to see what Elon says about the topic at hand and blindly parrot that line.
Technology 2
2
-
An open letter signed by 602 tech founders, VCs, and more urges Sequoia Capital act after Shaun Maguire said Zohran Mamdani “comes from a culture that lies about everything”
Technology 1
1
-
-
-
-