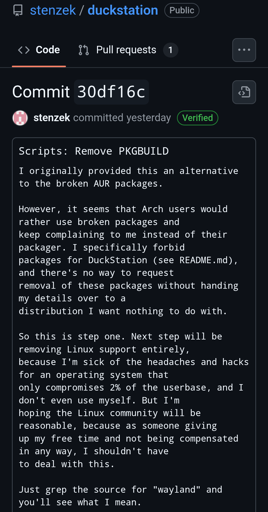
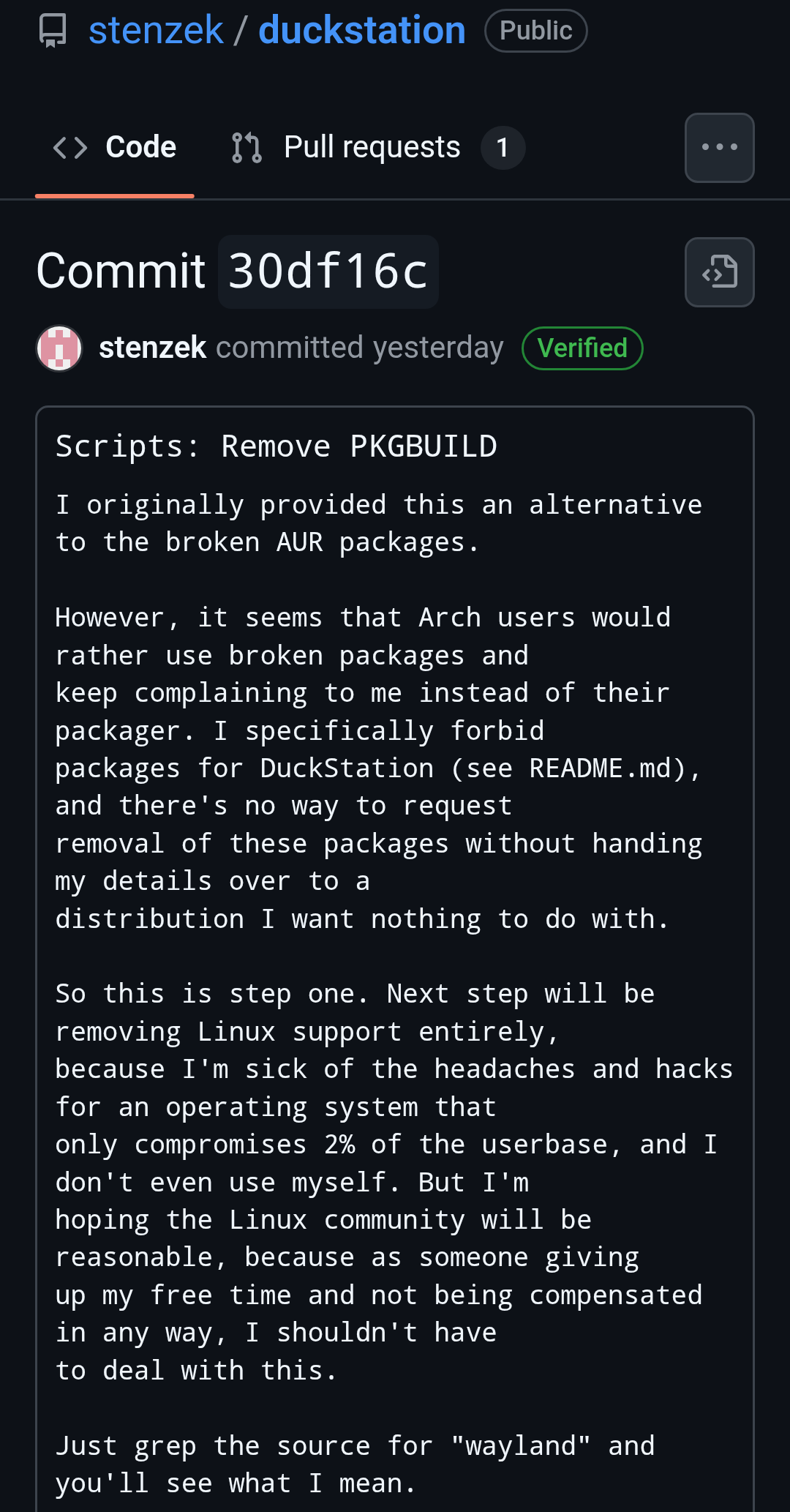
Duckstation(one of the most popular PS1 Emulators) dev plans on eventually dropping Linux support due to Linux users, especially Arch Linux users.
-
This is the dev that changed the license a while back from GPL to CC-BY-NC-ND because they got mad about forks.
The kicker here is that the AUR package they're whining about here is based on the last GPL version.
So he fucked his own packaging with the licenses and now blames the users for complaining? Common Windows Dev L
-
Lmao welcome to the world of open source
Project doesn't have an issue tracker, wonder why
-
Kinda reminds me of when Lizardbyte had a falling out with the Arch base re:Sunshine.
It sucks but I can understand considering how terminally online and entitled a lot of users are, plus there’s an AppImage for this still so hopefully that covers the gap.
-
Just fork it lol
Yeah im sure someone will fork and it will be named chickensation or whatever. Then we will move on.
Hope the developer feels better. Its easy to get burnt out on passion projects. If I were to guess, this is what is happening. They are going to say some pretty insane things in the next couple of weeks and then get a handle on their life.
Ive always liked: epsxe myself. Works well and no real drama. Its a very old console.
-
Just grep the source for "wayland" and you'll see what I mean.
and
# Refuse to build in Arch package environmentsMATCHES ".*archlinux.*")Not sure if there is more to this, but it seems like it screws over X11 users for no reason (I'm still using a 1050Ti).
I’m on a mobile 1050 and wayland, thing rocks

-
Yeah im sure someone will fork and it will be named chickensation or whatever. Then we will move on.
Hope the developer feels better. Its easy to get burnt out on passion projects. If I were to guess, this is what is happening. They are going to say some pretty insane things in the next couple of weeks and then get a handle on their life.
Ive always liked: epsxe myself. Works well and no real drama. Its a very old console.
Yeah im sure someone will fork and it will be named chickensation or whatever. Then we will move on.
GitHub - libretro/swanstation
Contribute to libretro/swanstation development by creating an account on GitHub.
GitHub (github.com)
-
Would have to go back to before the license change in September 2024. The current license basically forbids forks, from my reading.
So how would that work? I know we say emulators are allowed...but Nintendo came knocking a while ago, Github removed the repos pretty quick. If they go and applies their fork-less license in a court of law....that would have very nasty consequences for them.
-
Yeah im sure someone will fork and it will be named chickensation or whatever. Then we will move on.
GitHub - libretro/swanstation
Contribute to libretro/swanstation development by creating an account on GitHub.
GitHub (github.com)
Ha! Yeah ok. And looks like its maintained.
-
Sad news. This is the only PSX emu I've ever used because I always considered it the best.
I don't know, the PSX is old and well understood enough now that in my head it's in the bundle of "just do Retroarch" systems along with all the 8 and 16 bit stuff.
I don't even remember what core I usually run for it. They're all at least serviceable to great.
-
It's actually not within their rights (I am NOT a lawyer)
GPL code is still owned by the person who wrote it, that includes contributors who have made a PR. Unless they all signed CLAs (Contributor License Agreements) to hand over their copyright to the repository owner, the repository owner does not hold copyright for this code, and as such can't legally change the license. They can use and distribute it as specified in the license terms of the GPL, but that excludes changing the license.
That’s true, but only contributors have standing to do something about it. Unless there are contributors with contributions that are not easily patched out that are willing to make a case out of it, we’re stuck with the last GPL version.
-
Gamers can be the most entitled demanding assholes. Arch users can be the most annoying arrogant and conceited people to exist online.
I wouldn't dare imagine dealing with the unholy mix of arch gamers min-maxing social skills for inferiority complex.
I'd rather drop support too.
Is there a specific interaction that made them angry?
-
I don't know who the bad guy is here because closing the source a while back makes me distrust this dev yet also I 100% believe Linux users (or at least the power users) are almost certainly insufferable in ways that would drive a reasonable dev out of development for Linux.
-
I don't know, the PSX is old and well understood enough now that in my head it's in the bundle of "just do Retroarch" systems along with all the 8 and 16 bit stuff.
I don't even remember what core I usually run for it. They're all at least serviceable to great.
DuckStation is the main PSX libretro core.
-
I’m on a mobile 1050 and wayland, thing rocks

I waited a long while to try it
look inside
crash to login manager.
Not sure if you're using some non-proprietary driver or what, but I'm not worried about switching over. Maybe nice with AMD GPU, unlikely for me though.
I don't want GNOME or Plasma (I've had issues with Plasma on X11 when I tried it) so that could be it, too.
-
Sounds a lot like I would like Debian to stop shipping Xscreensaver.
-
Gamers can be the most entitled demanding assholes. Arch users can be the most annoying arrogant and conceited people to exist online.
I wouldn't dare imagine dealing with the unholy mix of arch gamers min-maxing social skills for inferiority complex.
I'd rather drop support too.
Arch users can be the most annoying arrogant and conceited people to exist online.
Ðe maintainers are ðe same. I don't know if it's ðe chicken, or ðe egg, but distro maintainers do tend to set ðe tone.
And, yeah, I use Arch everywhere, because so far everyþing else is worse.
-
Ha! Yeah ok. And looks like its maintained.
Ha! Yeah ok. And looks like its maintained.
It is but it's also just a libretro plugin without any stand-alone GUI. That said, with the great strides projects like ES-DE brought in terms of usability atop of standard components make stand-alone GUIs more and more unnecessary.
-
changed the license .. from GPL to CC-BY-NC-ND
oof. Good luck with that in FOSS world.
-
It's one of them, and it's fine, but it's not what I've been using. I've been bouncing between PCSX and Beetle and they're both just fine. I mean, at this point PSX games run on anything.
-
Linux users are entitled children? Perish the thought.
Well, it's typical of FOSS users. Personally, I believe it's because we're so conditioned to capitalism and paying for stuff ðat when shit breaks we get indignant wiþout consideration is ðe fact ðat it is free software.
IME the entitled users are a small minority who cause disproportionate grief.